Reference no: EM131357004
A description of fourteen typical information processing routines is given here, along with ten numbered excerpts from systems flowcharts (see given Figure).
Match the flowcharting segments with the descriptions to which they correspond. Four descriptions will be left blank.
a. Data on source documents are keyed to an offline disk.
b. A deposit slip and check are sent to a customer.
c. A printed output document is filed.
d. Output is sent to a computer screen at a remote location.
e. A clerk manually posts sales orders to the outstanding order data store.
f. A report is printed from the contents of a master data store.
g. Data stored on a disk is sorted and placed on another disk.
h. Data on a magnetic tape are printed during an offline operation.
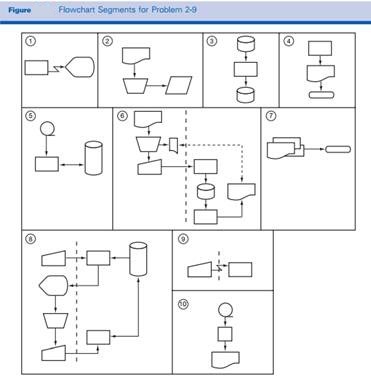
i. Data are keyed from a terminal at a remote location.
j. A batch total is compared to the total reflected on an error and summary report.
k. Magnetic tape input is used to update master data kept on a disk.
l. The cash receipts summary report is sent by the accounts receivable department to the general ledger department.
m. Input stored on two magnetic disks is merged.
n. Programmed edits are performed on key input, the data entry clerk investigates exceptions and keys in corrections, then the master file is updated.
|
Which machine tim should recommend
: Tim Smunt has been asked to evaluate two machines. After some investigation, he determines that they have the costs shown in the following table. Determine, via the present value method, which machine Tim should recommend
|
|
Construct a context diagram based on the table
: Prepare a table of entities and activities based on either the Lincoln Company or the Bono Insurance narrative.- Construct a context diagram based on the table you prepared in part a.
|
|
Describe some of the unorthodox strategies covered by terris
: Describe some of the unorthodox strategies covered by Terris during this era that made Lockheed become "...a byword for the shady practices of American multi-national corporations, and major impetus for new legislation...".
|
|
Percent growth rate in its dividends indefinitely
: The Absolute Zero Co. just issued a dividend of $2.60 per share on its common stock. The company is expected to maintain a constant 5.4 percent growth rate in its dividends indefinitely. If the stock sells for $52 a share, what is the company’s cost ..
|
|
Match the flowcharting segments with the descriptions
: Match the flowcharting segments with the descriptions to which they correspond. Four descriptions will be left blank.- Data on source documents are keyed to an offline disk.
|
|
First investment occurs at end of your first year of work
: Assume that you have 40 years until retirement and have just started your first job. Once you retire, you anticipate that you will live for 30 additional years. Assume that you will require $100,000 per year to support yourself in retirement. Assume ..
|
|
What in your mind is the right thing to do
: What in your mind is the right thing to do? What is value of having an ethics program and what are responsibilities of front line leaders/supervisors and the workers when they face dilemmas such as the one described?
|
|
Summarize the key points presented in the article
: Summarize the key points presented in the article.Describe the key elements of a solid emergency response program.Discuss why proper decontamination of victims is important.Discuss your opinion or what you can conclude from the article.
|
|
Which option has the highest expected monetary value
: James Lawson's Bed and Breakfast, in a small historic Mississippi town, must decide how to subdivide (remodel) the large old home that will become its inn. Which option has the highest expected monetary value
|