Reference no: EM13995052
INFA 630
Intrusion Detection and Intrusion Prevention
Dr. Stephen Gantz, CISSP-ISSAP, CEH, CRISC, CIPP/G, C|CISO
Midterm Exam
Instructions
You are to take this test during the week of October 26 - November 1, 2015. Work alone. You may not confer with other class members, or anyone else, directly or by e-mail or otherwise, regarding the questions, issues, or your answers. You may use your notes, textbooks, other published materials, the LEO site for this class, and the Internet.
The test is worth 25% of your grade for the course. It is scored on the basis of 100 points for the test. The exam is intended to assess your understanding of key concepts in the course, NOT your ability to look up concepts in the textbook. Wherever possible, make sure answers are stated in your own words, and where applicable provide your own examples, rather than repeating the ones used in the course materials.
When composing your answers, be thorough. Do not simply examine one alternative if two or more alternatives exist. The more complete your answer, the higher your score will be. Be sure to identify any assumptions you are making in developing your answers, and describe how your answer would change if the assumptions were different.
While composing your answers, be VERY careful to cite your sources. It is easy to get careless and forget to footnote a source. Remember, failure to cite sources constitutes an academic integrity violation. Use APA style for citations and references.
The test is due no later than 11:59 p.m. Eastern Standard Time on November 1, 2015. Your answers should be contained in a Microsoft Word, RTF, or compatible format document uploaded to your LEO Assignment folder. Be sure to put your name on the front of your exam. Your instructor will also find it somewhat easier to manage several dozen mid-term documents if you include your name in the title of your saved, completed exam document (e.g., INFA630_midterm_lastname).
General or logistical questions about the exam or these instructions should be posted in the Q&A Conference. Please submit specific or detailed questions regarding the exam to your instructor at [email protected]. If questions submitted via email are applicable to all, your instructor will post them in the Midterm Q&A discussion forum, without revealing their source.
Exam Questions
Part 1: True or False Questions. (10 questions at 1 point each)
1. T F Anomaly-based intrusion detection systems generate alerts based on deviations from "normal" traffic. Answer: _____
2. T F A host-based IDS monitors only network traffic destined for a particular computer. Answer: ____
3. T F When discussing IDS and IPS, a signature is a digital certificate used to identify the author of a rule. Answer: _____
4. T F To comply with network communication standards, software running on Internet hosts must implement both IP and ICMP protocols. Answer: _____
5. T F Signature-based intrusion detection can identify previously unknown attacks. Answer: _____
6. T F The primary difference between network-based IDS and IPS is that an IPS responds to suspected attacks by blocking network traffic, while an IDS only provides notification that suspicious traffic is observed. Answer: _____
7. T F Snort requires the use of at least one preprocessor to be able to analyze patterns in network traffic spanning multiple packets. Answer: _____
8. T F Snort generates an alert as soon as a detection rule is matched. Answer: _____
9. T F A network-based IDS that scans packet traffic to try to match known attack patterns is called a signature-based NIDS. Answer: _____
10. T F An in-line IDS must have the processing power to handle traffic at least as fast as the bandwidth of the network it monitors, or it will lose packets and potentially fail to notify on packets matching alert rules. Answer: _____
Part 2: Multiple Choice Questions. Print the correct answer in the blank following the question. (Scored as 2 points for each question; there is exactly one correct choice for each question.) (5 questions at 2 points each)
1. Which of the following is an advantage of anomaly-based detection?
a. Rules are easy to define
b. The data it produces can be easily analyzed
c. It can detect "zero-day" or previously unknown attacks
d. Malicious activity that falls within normal usage patterns is detected
e. Rules developed at one site can be shared with many other users
Answer(s): ____
2. Most commercial NIDS tools generate alerts based on signatures at the network layer and what other OSI model layer?
a. Application layer
b. Presentation layer
c. Data-link layer
d. Transport layer
e. Session layer
Answer(s): _____
3. Potentially troubling causes for network traffic with out-of-order packet arrival include all of the following EXCEPT?
a. The network route for inbound packets is different than the outbound route
b. The packets were routed through a network that uses small packet size
c. The packets have been altered in transit before arriving
d. The packets sent from the source were split across multiple interfaces
e. The packets were transmitted using a connectionless protocol
Answer(s): _____
4. Which is/are true for intrusion protection systems (IPSes)?
a. An IPS detects network attacks and issues alerts
b. An IPS responds to network attacks by blocking traffic and resetting connections
c. An IPS is typically deployed inline to monitor traffic
d. a and b only
e. a, b, and c
Answer(s): _____
5. Which of the following is a limitation of Snort?
a. Cannot be centrally monitored with sensors running on different OSes
b. Cannot protect against insider threats
c. Cannot inspect encrypted traffic for attack signatures
d. Cannot scale effectively to protect a large network
e. Cannot detect application-layer attacks
Answer(s): _____
Part 3: Short Answers. Please answer briefly and completely, and cite all sources of information. (6 questions at 10 points each)
1. Compare and contrast signature-based and anomaly-based network intrusion detection systems. In your analysis, describe at least three ways in which the two types of IDS are similar, and at least three ways in which they differ.
2. Identify and briefly describe the two primary approaches to developing signatures for network-based IDS tools. Is one technique preferred over the other? Explain why.
3. Describe what a pre-processor does in a network-based IDS tool such as Snort. Demonstrate your understanding of this functionality by citing two examples of pre-processors and explaining what function they serve in the process of network traffic analysis and intrusion detection.
4. If an attacker knew a network-based IDS like Snort was running in a targeted environment, how might the attacker try to evade detection? Provide at least two examples of IDS evasion techniques that might be used by an attacker, and suggest a remedy or defense against the techniques you cite.
5. Describe how host-based intrusion detection works, briefly contrasting it with network-based intrusion detection. Explain three types of threats against which HIDS is particularly effective.
6. Examine the following screen-shot of a short packet capture in Wireshark. Describe the sequence of packets exchanged between the two systems participating in the conversation. What sort of traffic has been captured? What is happening in the sequence shown on the screen?
Screen-shot for question 6.
Part 4: IDS Placement. (20 points) Please refer to the accompanying network diagram as you consider and respond to the following:
Global Corporation, Inc. (GCI) is a fictional company providing business services to a variety of clients across many industries, including commercial and government entities. GCI recently finished construction of a new corporate headquarters, which includes the network infrastructure for primary company operations. You are a security analyst specializing in intrusion detection brought in by GCI to help determine the most appropriate kinds of IDS to use and most effective IDS placements to protect their network.
GCI's network uses a conventional three-zone architecture: devices exposed to the Internet are part of an un-trusted outer zone; Internet-accessible services such as the company website and email are in a demilitarized zone; and major systems and servers supporting both Internet-facing and internal applications as well as internal computing resources such as the corporate LAN are in a trusted zone. Each of these zones is segmented from the others using hardware-based firewalls; the corporate databases are further protected behind their own dedicated firewall. GCI allows employees remote access to the corporate LAN using either VPN or dial-up connections.
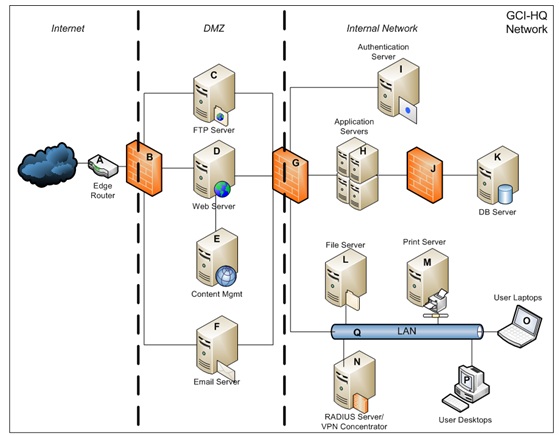
Identify the locations throughout the GCI network where you would recommend IDS to be deployed. Each of the components in the accompanying GCI-HQ Network diagram is lettered to simplify your references to the diagram. For network connections between devices and layers, you may assume for the purposes of this exercise that all components in a given zone share the same network segment. For each placement you recommend, please note the type of IDS to be deployed and any specific considerations that should be taken into account to ensure the effective monitoring of the location.