Reference no: EM131272964
Information Security - Project Symmetric Cipher
Symmetric Cipher / Implement the encryption algorithm
• Consider the following encryption algorithm
- Key size: 32 bits
- Block size: 48 bits
- Structure: SP-Network with 10 rounds
- S-box is the same as AES
- M: Linear Transition
• M is a 3x3 matrix in GF(28)
• GF(28) is the same field in AES
-p(x) = x8 + x4 + x3 + x1 +1
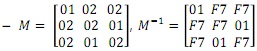
• Consider the following encryption algorithm (cont.)
- Key Schedule
• Rotl(x, n): n-bit circular left-shift of x
• Generate W (544-bit length) from a master key K
W = K || K0 || k1 || .... || k15
= K || Rotl(K,5) || Rotl(K,10) || Rotl(K,15) || ... || Rotl(K,11) || Rotl(K,16)
• Generate rk0, rk1, rk10 by extracting leftmost 48-bit from W
- Use only 11 (528-bit) keys and throw out the rest 16-bit
1. Implement the encryption algorithm
- Express the matrix multiplication as a linear combination of vectors
- Define three tables and store them in advance
Takes as input a byte value and produces a column vector that is a function of the S-box entry for that byte value
- Implement using the table lookup operations, XOR operations per column per round
2. Find the key K
- E(K, 0x0123456789AB) = 0xFBD040D6DB9C and
- E(K, 0x9A6BCC10E84A) = 0xE5CBFFF7E08B
|
State the reasons for applying to the philanthropy
: Revise the given document.- Given the document is about:- State the reasons for applying to the Philanthropy and Voluntary Service, and what you would gain personally, professionally and academically be attending.
|
|
Describe the data breach incident of the data breach
: Describe the data breach incident and the primary causes of the data breach. Assess if there are deficiencies in the regulatory requirements and whether they need to be changed, and how they need to be changed.
|
|
Describe one evidence claim for and claim against
: Describe one (1) evidence claim for and one(1) evidence claim against your chosen topic. The topic is "What are the unconstructive and constructive impacts of technology on the teenagers"?
|
|
Explain the power of social influence based on the findings
: Explain the power of social influence based on the findings of Milgram's experiment. Provide one (1) example of a situation you have been in where you felt you had to conform to someone or something. Indicate whether you felt you had to conform be..
|
|
Implement the encryption algorithm
: Implement the encryption algorithm and - Express the matrix multiplication as a linear combination of vectors and Define three tables and store them in advance
|
|
Identify two human and technological protective measures
: Identify two to three human and technological protective measures that you would use as security safeguards and enforcement actions in order to address the ethics issue that you have chosen.
|
|
Is there a maturational or developmental aspect to it
: Is there a historical or cultural context to this? (I.e. Freud was his mothers favorite, as well as living and writing during repressed Victorian tines and WWI and WWII; Behavioral and CBT approaches evolved during a time that people wanted to mak..
|
|
What types of goals are suitable for diversity training
: What types of goals are suitable for diversity training and How might a complete performance management system differ from our annual performance appraisals.
|
|
Critical importance of an executive
: The market trend towards escalating executive compensation reflects the critical importance of an executive to an organization's long-term viability.
|