Reference no: EM13924383
1. The paper needs to address the following question; How secure are Cloud Computing?
2. The paper needs to create a security model (in theory) that will protection an organization database and information for as:
a. Receiving the data and document
b. Protecting data and document when it is stored
c. Protecting the information when it is distributed within the organization and other organization
d. etc
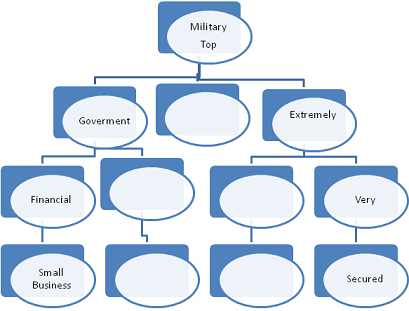
3. This model needs use three bytes layer of security for different organization such as:
a. Small businesses
b. Financial
c. Government
d. Military
e. etc
4. Use the following security standard to create a diagrams and graphs to show layers of security depending on level security required by each organization :
a. Secured
b. Very secured
c. Extremely Secured
d. Top level Secured
e. etc
5. See below graph to Start the idea for creating protocol security layers.
6. Chapter 3-4 needs to the body or fact of the paper.
7. I have attached a new paper to give you an example of what is needed.
8. The paper doesn't need to be 40 pages it can be 30 - 40 as long as it gets the message across, Give Problem, Create a Solution(s) and explain the Results.
9. The paper needs to have more graphs and statistical data with explanation.
10. I need one Chapter of the paper per week so he can check and approve it to move on to the next the chapter.