Reference no: EM131444893
Question 1. (a) Solve the given puzzle using crypt arithmatic method.
B A S E
+ B A L L
G A M E S
(b) Apply uniform cost search Algorithm on given graph.
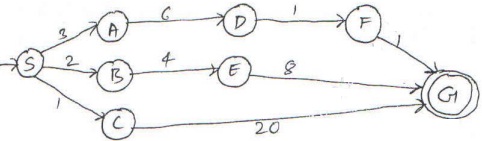
Question 2. (a) Consider the examples.
(i) If Triangle is equilateral then it is isosceles.
(ii) If Triangle is isosceles then two sides 'A' and 'B' are equal.
(iii) If 'AB' and 'AC' are equal then Angle 'B' and 'C' are equal.
(iv) ABC is an equilateral Triangle.
Prove that angle 'B' is equal to angle 'C' using inferencing techniques of modus ponen and Resolution.
Question 3. (a) Consider the knowledge base KB that contains the following propositional logic sentences.
Q ⇒ P
P ⇒ ¬ Q
Q v R
(i) Construct a Truth table trat shows the truth value of each sentence in KB and indicate the model in which the KB is true.
(ii) Does KB entail R ? Use the definition of entailment to justify your answer.
(iii) Does KB R ⇒ ¬ P entail ? Extend the truth table and usQ the definition of entailment to justify your answer.
(iv) Does KB Q ⇒ ¬ R entail ? Extend truth table and use the definition of entailment to justify your answer.
Question 4. (a) You have two neighbours, John and Mary, who have promised to call you at work when they hear the alarm. John always calls when he hears the alarm, but sometimes confuses the telephone ringing with the alarm and calls then, too. Mary on the other hand, likes rather loud music and sometimes misses the alarm altogether. Given the evidence of who has or has not called, we would like to estimate the probability of a burglary.
Draw a Bayesian network for this domain with suitable probability tables.
Question 5. (a) Consider the given Game Tree. Apply the Aplpha- Beta pruning algorithm and 10 decide, what is to be the next best move ? (Δ - max node , ∇- min node)
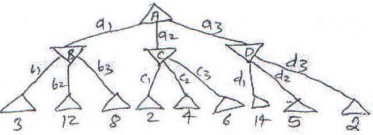
|
What are the sources behind temperamental differences
: In your words, define human development. What is its relationship to socialization/culture?What Is Temperament? Explain The Goodness of Fit Between Temperament and Culture. What are the sources behind Temperamental Differences?
|
|
What coverage do you think your company has and why
: What are the benefits of the coverage? Who is eligible for coverage? How is the coverage financed? What coverage do you think your company has and why?
|
|
Specific heat of copper
: An electric current heats a 335 g copper wire from 25oC to 100.oC. How much heat was generated by the current? The specific heat of copper is 0.390 J/(g.Co).
|
|
Describe how your firm compares with the industry
: BUS650- Identify where your firm seems to lag. Describe how your firm compares with the industry and speculate as to why you believe your firm is performing as it is.
|
|
Estimate the probability of a burglary
: BEITC703 - Solve the given puzzle using crypt arithmatic method and Construct a Truth table trat shows the truth value of each sentence in KB and indicate the model in which the KB is true.
|
|
Calculate the value of bond a if the required return
: Calculate the value of bond A if the required return is (1) 8%, (2) 11%, and (3) 14%. Calculate the value of bond B if the required return is (1) 8%, (2) 11%, and (3) 14%.
|
|
Does the electron gain or lose energy
: The charge carried by an electron is -1.60×10-19 C. Suppose that an electron moves through a voltage of 120V from the negative polarity to the positive polarity. How much energy is transferred? Does the electron gain or lose energy?
|
|
Determine the magnitude of the net charge
: A 5-μF capacitor has 100 V between its terminals. Determine the magnitude of the net charge stored on each plate and the total net charge on both the plates.
|
|
Multiple of earth mass
: Spectroscopic studies indicate that the outermost particles have a speed of 17 km/s.Using the data in this problem, find the mass of Saturn. Express your answer result in kgand as a multiple of Earth's mass, ME
|