Reference no: EM13866857
C Programming Applications: Project
Objective:
You're working as an analyst at your organization's Security Operations Center (SOC). One of the other analysts was investigating alerts on a Windows host that indicated that the computer is infected. That analyst retrieved a PCAP of network traffic from the network. PCAP (Packet Capture) is a protocol for wireless Internet communication that allows a computer or device to receive incoming information from another device and convert that into usable information.
You've been asked to review the PCAP file and determine the IP address of the computer that was compromised, in addition to all possibly malicious IP addresses to which the system connected after the infection.
Phase 1: Read Data
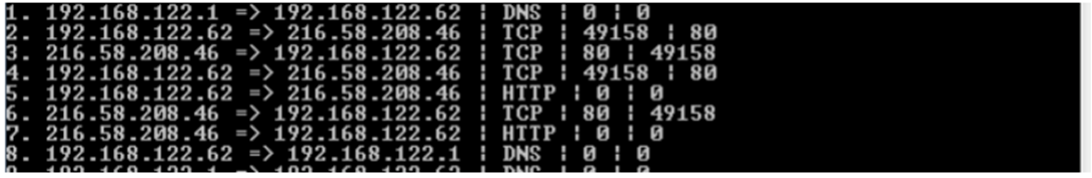
The PCAP file has been processed with software called WireShark to convert the binary information into ASCII text that is in a Comma Separated Value (CSV) file. For this phase, you will read the Source IP, Destination IP, Protocol, Source Port and Destination Port for each node in the network into individual arrays. The source and destination port are not columns in themselves, but are part of the description (sometimes). Make sure to do the following:
• Use a symbolic constant to set the maximum number of nodes for each array to 5000
• All arrays are declared globally
• Create a function GetData() to open and read all content into the global arrays
• Display the total number of lines read (should be 1978)
• Confirm all the data is being read correctly and displaying all the information stored in the arrays
- Create a function called DisplayData(int sIndex, int eIndex) to display all the data. sIndex is the starting index of the arrays to display, and eIndex, is the last index to display. Use the format below.
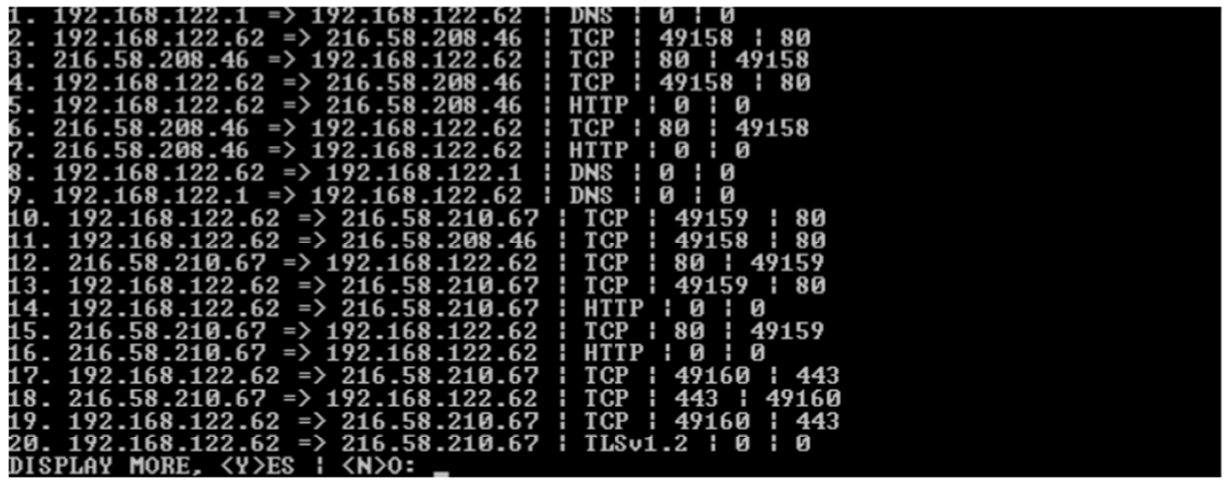
Extra Credit (+10): Display only 20 lines at a time. After each block of 20, display the text "DISPLAY MORE <Y>ES I <N>0". If the user enters anything that is not N (case insensitive), then display the next block of 20. If they enter `N" (case insensitive), then stop displaying the output.
Phase 2: Read the Black and White list files
The file blacklist.csv contains a list of IP addresses that are known to be malicious by a security company (typically these type of files contain hundreds of thousands of entries). Read the IP addresses of these systems into an array (you do not need the description of each IP). Similarly, the file whitelist.csv contains a list of IP addresses that are known to be benevolent. Typically, we only need to know the domain of the system (the first octet of the IP addresses) that way we can flag all IP addresses from that domain as safe. Because of this, this file contains Xs in the last three octets of the IP address.
Phase 3: Find the Infected Node
In this phase you will check each of the destination IP addresses against the Black List to identify any nodes that communicated with this malicious systems.
• Create a function called FindInfectedNode()
• Store the first source IP where the correspond destination IP is located within the Black List in an array called targetMachine
• Use the DisplayData function to display all the information for this system.

Phase 4: Infected System Traffic
Your next task is to extract all the traffic from the infected node that is not on port 80 (regular HTTP interne traffic).
• Create a function IdentifyInfectedSystemTraffic()
• Create an array to store identified destination IP addresses from the infected system
• Find all traffic from the infected system which took place on a port other than 80 and add only unique IP addresses to the array (no duplicates)
• Display this list to make sure its correct.

Phase 5: Clean Infection Traffic
The list of connections from the infected system needs to be cleaned to remove systems that are most likely not malicious.
• Create a function CleanInfectedSystemTraffic()
• Identify IPs that are from the same subnet as the infected system (the first octet of the IP address is the same) as well as IP domains (first octet) from the White List
• Remove these IP addresses from the list of IP addresses of traffic from the infected system.

These remaining systems are all potential malicious addresses that will be further analyzed in the next project.
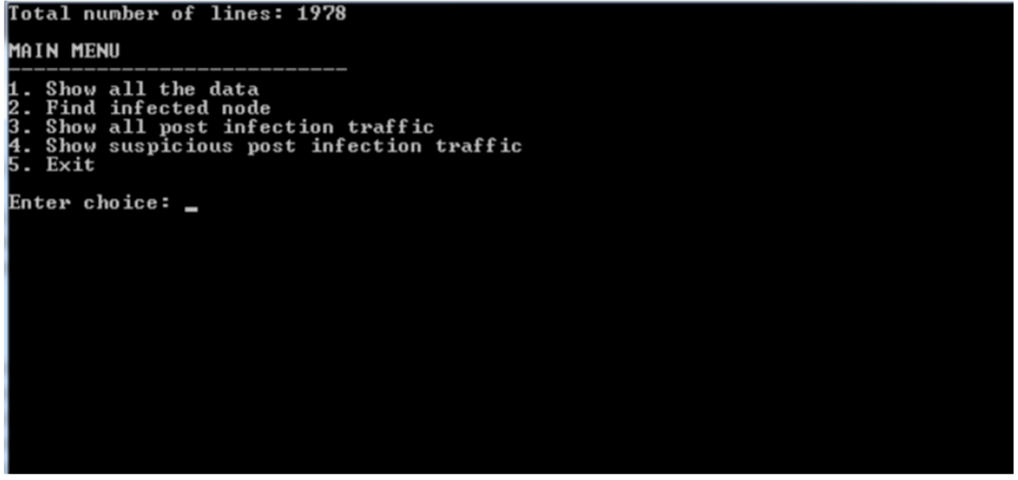
Phase 6: Main Menu
Create a menu to ask the user to enter a choice from 1 - 5. Make sure to employ proper input validation to ensure the user can only enter a valid choice. If the user enters an invalid choice, indicate as much, and then redisplay the menu. Link each menu to display the output from the matching phase.
Attachment:- C-programing.rar