Reference no: EM131220953
Operating Systems- Homework
Purpose
The purpose of this exercise is to understand how creating files affects the available disk space and the available i-nodes on a disk partition on Linux/UNIX.
Assignment
Create and leave a copy of your C program for this assignment on Pond under cs351/hw4.
1) Write a C program on Pond that:
a. Accepts 2 command line inputs: number of files to create, size of each file (in bytes). For example run your program as ./hw4 10 20 will create 10 files of size 20 bytes each. Your program should check and report not only incorrect # of arguments, but also invalid argument values, such as zero or negative.
b. Creates that many files named after your first name (yourname0, yourname1, yourname2... ) and writes the required number of bytes to each file. One simple strategy is to write that many number of characters since each character is one byte. The content of the files isn't important, just the size. Use ls -l to see the result and verify files of correct size were created.
c. After your program is debugged, delete all files created by your program on Pond before moving to next steps. Use command rm command to delete all files. For example rm crystal* will delete all fines whose name start with crystal.
If you think step 1 is too hard, request a copy of the C code from instructor and directly start from step 2 for this assignment. Of course you will receive 0 pts for the C code part of this assignment.
Before moving on to the next steps, do some research on the UNIX/Linux command df. Understand what df does, its usage, and what it outputs.
2) Run the commands
df .; df -i .
to find out how many disk blocks and i-nodes are in use. Save the results (and future results) to document your answers. Be aware that that 1K-blocks is for display purpose only and is not the real block size of Pond file system. The actual block size is bigger.
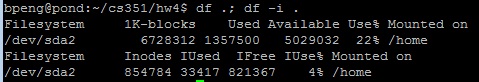
Read question (a) in step 12 before proceeding to step 3.
3) Run your program and create 10 files, each with 7 characters. Repeat step 2.
4) Run your program again and create 10 files, each with 13 characters. These 10 files will overwrite the 10 files you created in last step as they have the same names. So you still get 10 files under your working directory. Repeat step 2.
5) Run your program again and create 10 file, each with 25 characters. Repeat step 2.
6) You should be able to answer question (a) below now.
7) Delete the 10 files you just created. Repeat step 2.
8) Run your program and create 10 files, each with 8,192 characters.
9) Repeat step 7.
10) Run your program and create 10 files, each with 8,193 characters.
11) Repeat step 7.
12) Using your results, write a few paragraphs explaining each question below. Be specific. For example if list the numbers in comparison or examples involved to support any statement you make.
a. How creating the same files over and over (steps 3-5) affects disk block usage. Do you think the directory entry is reused when a new file overwrites an existing file of the same name? What about i-nodes? What about data blocks? How can you tell?
b. What difference you see when creating 8,192 byte files vs. 25 byte files. Be specific.
c. What difference you see when creating 8,193 byte files vs. 25 byte files. Be specific.
d. How creating any new file affects i-node usage. How can you tell?
e. What is the block size for this disk partition? How can you tell? If necessary try creating more files of different sizes.
f. How is it possible for a program to fail to create a new file on a file system using i-node, even though there are many free blocks still available? Hint, if your answer doesn't include the word i-node, it's not getting full credit