Reference no: EM13189666
Question 1:
MIPS assembler
Please convert to MIPS assembler.
int is_more_than_a_dozen(int a, int b) {
if (sum(a, b) > 12)
return 1;
else
return 0;
}
int sum(int a, int b) {
return a + b;
}
Question 2:
MIPS instruction set I
Please convert to C. $s6 contains the base address of an array.
Loop: sll $t1, $s3, 2
add $t1, $t1, $s6
lw $t0, 0($t1)
bne $t0, $s5, Exit
addi $s3, $s3, 1
j Loop
Exit:
Question 3: MIPS instruction set II
Assume that the loop is placed at location 60000 in memory, what is the machine code for the loop given above?
Please write out the machine code in two columns, the ?rst as decimal values, the second as a binary number.
Please keep inmind thatMIPS instructions have byte addresses, so addresses of sequentialwords differ by 4. bne will jump relative to the following instruction. j does use the full address, but make sure it jumps to words not bytes.
Question 4: Bitpattern
In a VonNeumann architecture, groups of bits have no intrinsicmeanings by themselves. The following table shows bit patterns expressed in hexadecimal notation. Please answer the questions below for each bit pattern.
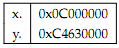
What decimal number does the bit pattern represent...
a) if it is a two's complement number?
b) if it is an unsigned integer?
c) if this bit pattern is placed into the Instruction Register, what MIPS instruction would be
d) if it is an IEEE 754 ?oating point number?
Question 5: Floating point binary representation
Please compute the IEEE754 binary representation of the following numbers
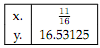
Please provide the complete calculation, not just a result. For y: you can use the algorithm shown in the example output of a conversion program.
|
What is the equivalent uniform annual cost of the 20-year
: Maintenance expenditures for a structure with a 20-year life will come as periodic outlays for overhaul of $4,000 at the end of the 5th year, $6,000 at the end of the 10th year, and $7,500 at the end of the 15th year. With interest at 8%, what is ..
|
|
What fiscal policy and monetary policy would be appropriate
: Write your individual answers to the questions listed above together in essay format (minumum of 300 words combined in APA style), using correct economic terms covered in the discussions. If you only write 300 words, you probably won't be able to ..
|
|
Discuss how to write the demand curve
: In Bayonne, NJ there is a large beauty salon and a number of smaller ones.The total demand function for hair styling per day is Q=180 - 10P, where P is in dollars The marginal cost function of all the small salons together is SMCf = 4+ 0.1Q
|
|
Calculate the hhi for the industry
: Calculate the four-firm and six-firm concentration ratios for the computer industry. Calculate the HHI for the industry. Suppose that Appel Computer and Banana Computer were to merge with no change in the sales of any of the different computers. C..
|
|
Convert to mips assembler
: Please provide the complete calculation, not just a result. For y: you can use the algorithm shown in the example output of a conversion program.
|
|
Explain how the problems are interconnected.
: Among the problems that hinder growth in developing economies are poor infrastructure, lack of financial institutions and a sound money supply, a low saving rate, poor capital base, and lack of foreign exchange. Explain how these problems are inte..
|
|
Which statement(s) would you use?
: How would you use the financial statement to determine when to the need for the purchase of inventory?
|
|
Divide the calculations equally and the slides equally
: Gary and Diane must prepare a presentation for their marketing class. As part of their presentation, they must do a series of calculations and prepare 50 PowerPoint slides. It would take Gary 10 hours to do the required calculation and 10 hours to..
|
|
Describe at least two actions a manager can take
: Describe at least two actions a manager can take to protect her or himself and the organization she or he represents from a tort lawsuit.2. Create a list of five best practices that managers in most industries could take to protect the privacy of ..
|