Q. What are the Logic Micro-operations?
Logic operations are fundamentally binary operations that are performed on string of bits stored in the registers. For a logic micro-operation every bit of a register is treated as a variable.
A logic micro-operation:
R1 ← R1.R2 specifies AND operation to be performed on contents of R1 and R2 in addition store the results in R1. For illustration if R1 and R2 are 8 bits registers and:
R1 comprise 10010011 and
R2 comprise 01010101
Then R1 will comprise 00010001 after AND operation.
Some of the common logic micro-operations are AND, OR, NOT or Complement, Exclusive OR, NOR and NAND. In many computers only four: AND, OR, XOR (exclusive OR) and complement micro-operations are implemented.
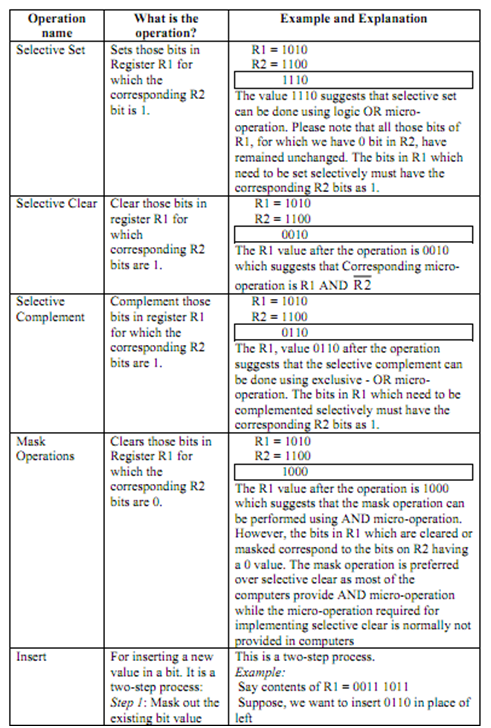
Let's now discuss how these four micro-operations can be employed in implementing some of significant applications of manipulation of bits of a word like changing some bit values or deleting a group of bits. We are presuming that resultof logic micro-operations go back to Register R1 and R2 comprises the second operand.
We will play a trick with manipulations we are performing. Let's select 1010 as 4 bit data for register R1 and 1100 data for register R2. Why? Since if you see bit combinations of R2 and R1 they represent the truth table entries (read from right to left and bottom to top) 00, 01, 10 and 11. So resultant of logical operation on them will signify which logic micro-operation is required to be performed for that data manipulation. The below table gives details on some of these operations:
R1 1 0 1 0
R2 1 1 0 0