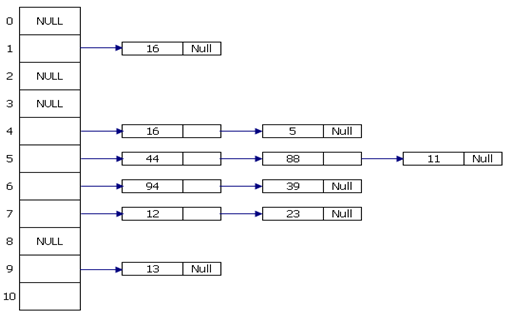
Q. Make the 11 item hash table resulting from hashing the given keys: 12, 44, 13, 88, 23, 94, 11, 39, 20, 16 and 5 by making use of the hash function h(i) = (2i+5) mod 11.
Ans.
The size of the table is 11
h(12) = (24+5) mod 11 = 29 mod 11 = 7
h(44) = (88+5) mod 11 = 93 mod 11 = 5
h(13) = (26+5) mod 11 = 31 mod 11 = 9
h(88) = (176+5)mod 11= 181mod 11 = 5
h(23) = (46+5) mod 11 = 51 mod 11 = 7
h(94) = (188+5)mod 11= 193mod 11 = 6
h(11) = (22+5) mod 11 = 27 mod 11 = 5
h(39) = (78+5) mod 11 = 83 mod 11 = 6
h(20) = (40+5) mod 11 = 45 mod 11 = 1
h(16) = (24+5) mod 11 = 29 mod 11 = 4
h(5) = (10+5) mod 11 = 15 mod 11 = 4