Question:
(a) The diagram below shows a configuration of Internet routers (A-F) which achieve dynamic routing through the use of a Distance Vector routing algorithm. The metric used is a simple hop-count (if two equal-length routes are available then the one via the lower numbered interface is chosen)
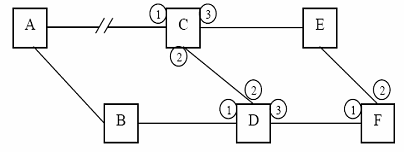
The link between A and C has been broken for some time and routing has stabilised to accommodate the situation. Each router maintains a routing table like the one below:
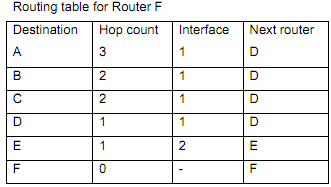
(i) Give the current routing table for Router C
(ii) Router D now discovers that the link between B and D has broken. Immediately after this (i.e. before D has reported the fact to any other routers), D receives distance vectors from C and F based on their current routing tables. Clearly outline the reasoning that D would use in calculating its new routing table entry for node A following receipt of the distance vectors from C and F.
(iii) How will C's routing table for node A be amended next time it receives a distance vector from D? What problem of distance vector algorithms does this illustrate?
(iv) How is this problem handled?
(b) Bridges do not have to be manually configured. Describe how the bridge learns about the different computers connected. Assume a bridge connected to two LAN segments. Illustrate your answer using a typical filtering table.
(c) What protocol can a station operating in a TCP/IP network use to discover the IP address of a computer A when it knows only the physical address of A?
(d) Assume that the OSI-based protocol of the LAN of an organization needs to provide the services of: physical transmission, point-to-
point flow control, end-to-end delivery, data encryption and compression as well as network access interfaces. Which layers of the OSI model does this protocol need to implement?