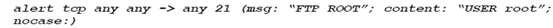Let's consider the network shown in Figure 1 where Snort is deployed.
In Figure 1, why is Snort deployed in the DMZ instead of the Internal Network?
In Figure 1, say True or False to the following statement: "Snort can see both incoming packets from the left firewall and outgoing packets from the right firewall".
In Figure 1, assume a packet P matches the following Snort rule when the packet is analyzed by Snort.
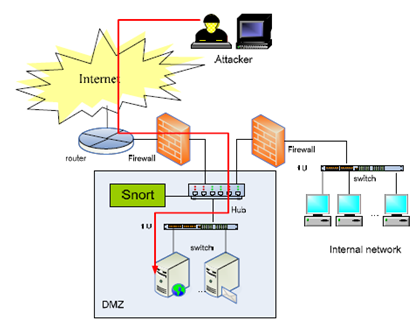
Is packet P a TCP packet or a UDP packet?
Is packet P an incoming packet or an outgoing packet?
What is the source IP address contained in the header of packet P?
What is the destination IP address contained in the header of packet P?
Who is the receiver program of this packet?
The payload of packet P must contain four specific bytes. What are the four specific bytes?
Since packet P matches the rule, an alert will be raised and the Security Administrator will receive a notice (message) from Snort. What will the notice say to the administrator?
A Phf attack is a remote to local (R2L) attack against the Web Server running the "Phf" CGI script. Phf script has vulnerability that, when exploited, allows remote users to execute arbitrary commands on the Web Server and such commands will be written as:
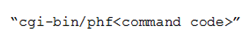
Attackers can launch this attack from any PC connected to the Internet, and the target system can be any apache web servers that permit access to the Phf script. Let's assume that the Web Server shown in Figure 1 (inside DMZ) is an apache web server that permits Phf scripts and let's assume the IP address of the Web Server is 195.4.12.5. Please give a concrete Snort rule that can detect Phf attacks against the Web Server.
To be able to detect attack packets, Snort firstly needs to log the corresponding traffic. For this purpose, the Snort administrator will need to set up several log rules. Please give a log rule to let Snort log UDP traffic from any IP address with any port going to computers on the Internal Network specified with a Class C IP range 195.4.13.0/24.
Explain the meaning of the following Snort rule.