QUESTION
a) Below is a capture of an Ethernet II frame which contains an IPv4 packet and a segment. Give the source MAC address in hexadecimal; the source IP address, the upper layer protocol, the TTL and the header checksum in decimal; the source port number in decimal and hence deduce the application layer protocol this segment is destined to.
00 13 02 4a 88 97 00 15 56 3a 4c 79 08 00 45 00
00 9e 99 e6 40 00 3c 11 15 fd ca 7b 02 06 c0 a8
01 42 00 35 04 01 00 8a 35 9f
b) A UTM graduate has been told by his supervisor to work out how to connect a small university campus onto the Internet.
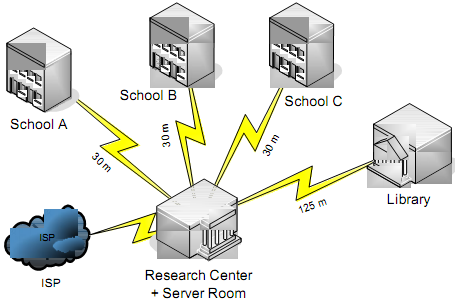
The campus contains 3 schools, a library and a Research Centre. Each school has about 300 hosts, 50 for staff, and 250 for students.
The library consists of 4 levels. At any one time, a maximum of 50 WiFi-ready laptops are loaned to students for use within the library only.
The Research Centre has 12 workstations which run simulation software requiring an internal bandwidth above 500 Mbps.
The campus has a HTTP server and a FTP server holding the web content, both of which should be accessible internally and externally.
The university's ISP has awarded one block of public IP addresses as 202.123.21.112 /29.
Provide a suitable network infrastructure for the campus bearing in mind sound design principles. Give the configurations of all important nodes such as hardware devices or servers that you would be using to implement your design. Additionally, give the network configuration of 1 staff PC from any school, 1 laptop from the Library. Be sure to mention topologies, technologies used in your design.