Q. Permutation representation through Matrix?

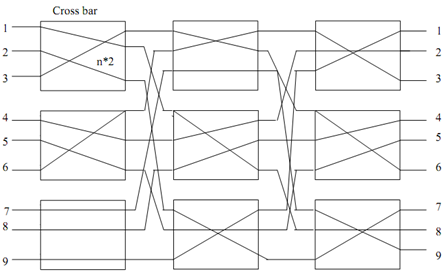
Figure: Clos Network
The functioning of this above permutation is displayed in Figure. This permutation is able to be represented by subsequent matrix too,
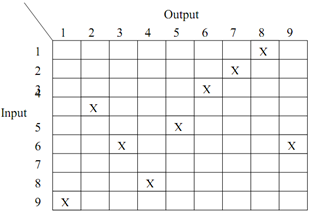
Figure: Permutation representation through Matrix
The upper input of all first stage switches will be connected with respective inputs of 1st middle stage switch and lower input of every first stage switches will be connected with respective inputs of 2nd switch. Likewise, all outputs of 1st switch of middle stage will be connected as upper input of switches at third stage. In Benz network to reduce the complexity the middle stage switches can recursively be broken into N/4 × N/4 (then N/8 × M/8), till switch size becomes 2×2.
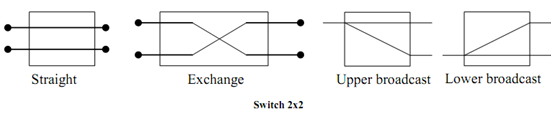
The connection in a 2×2 switch will either be straight, exchange, lower broadcast or upper broadcast as shown in the below Figure.
The 8×8 Benz network with all switches replaced by a 2×2 is shown in below Figure:
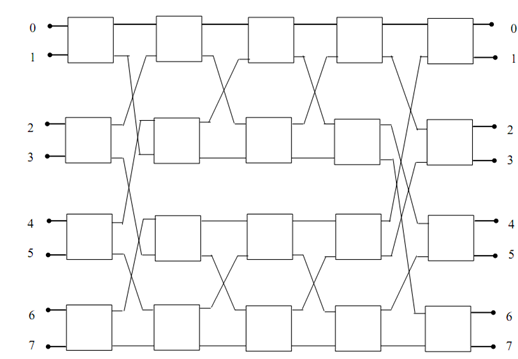
Figure: Benz Network
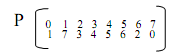
The Bens network connection for permutation
would be in this manner:-
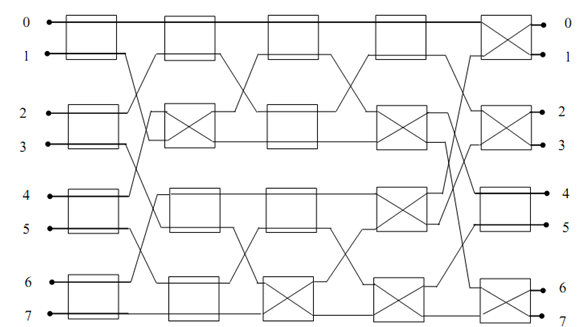
Figure: 8X8 BENZ NETWORK OF 4 STAGES
The permutation for P =  would be following manner:
would be following manner:
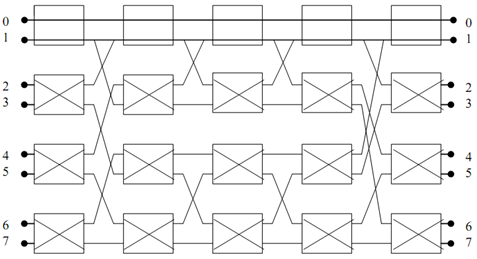
Figure: Line number for n