You have been asked to setup a remote temperature sensing system for an electric furnace. The system consists of a sensor unit which feeds an analogue signal to a PCM encoder. The resulting bit stream is then fed into a modem and the modulated signal is sent via a leased line across a PSTN to the monitoring room a few kilometres away as shown below:
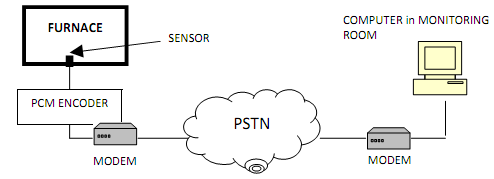
(a) Assuming that the sensor operates in the range or 900 °C to 1412°C which corresponds to +0 V and +1 V output respectively and has an operational bandwidth of 1,000 Hz. If the monitoring room wants to detect 32°C unit change in temperature of the furnace.
Calculate how many quantization levels are needed in the PCM encoder?
(b) What will be the minimum sampling rate needed to fully characterize the sensor signal?
(c) Hence, deduce the maximum bit-rate of this PCM set-up, assuming noiseless and error less conditions.
(d) Assume the modem uses 4-PSK modulation on a noiseless leased line with a bandwidth of 2000 Hz, deduce the Nyquist maximum data rate in bits per second.
(e) Assume that the leased line has a SNR of 9 dB, what is the maximum bit-rate achievable to the nearest bit?
(f) Assume in real-life, the data rate through the leased line is 5555 bps with a minimum bit error rate of 10-6. Deduce the minimum received signal strength in dBW that is required assuming a transmission media temperature of 25 °C. (Boltzmann's Constant k = 1.3803 X 10-23J/°K)