Consider the site-to-site VPN scenario shown in Figure 2. Let's deploy the AH protocol on the two VPN routers so that no desktop on the two sites need to do any AH operations. Assume Alice's desktop is on VPN Site 1 while Bob's desktop is on VPN site 2. Assume the IP address of Alice's desktop is 130.2.3.244; the IP address of Bob's desktop is 166.100.66.2.
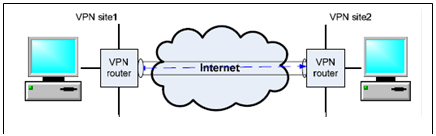
When Alice sends message "Stock X price $29" to Bob, the message sender program running on Alice's desktop needs to firstly compose the packet. Please draw the whole packet.
After a while, the packet will arrive at the VPN router on site 1. After the packet is processed by the VPN router according to the AH protocol, it will be sent out from the VPN router. When the packet leaves the VPN router on site 1, what does the packet look like? Please draw the whole packet. Please note that we assume the VPN router does not enforce the ESP protocol - no tunneling.
Let's assume there is a bad guy named Mallory who can intercept this packet in the Internet between these two VPN routers. When this packet is intercepted by Mallory, can Mallory know what the message is? Why?
After a while, the packet will arrive at the VPN router on Site 2. When the packet is processed by the VPN router on Site 2, what will the VPN router do? Please give a step-by-step answer.
To enforce an IP spoofing attack, Mallory will change the header of the packet before it arrives at the VPN router on Site 2. In particular, Mallory will replace the source IP with 130.2.8.3. Can this IP spoofing attack fool the VPN router on Site 2? Why? Note that Mallory will try his best to fake a hash to fool the VPN router.
If the IP spoofing attack mentioned in Question 1.5 is launched by a colleague employee of Alice inside Site 1, Can this IP spoofing attack fool the VPN router on Site 2? Why?