Q. Explain about Quine McKluskey Method?
A tabular method was proposed to deal with increasing number of variables called Quine McKluskey Method. This method is appropriate for programming and therefore provides a tool for automating design in form of minimizing Boolean expression.
The fundamental standard behind Quine McKluskey Method is to remove terms that are redundant and can be attained by other terms.
To understand Quine - Mc Kluskey method lets see subsequent illustration:-
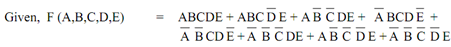
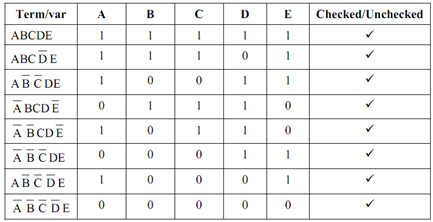
Step I: Terms of function are placed in table as below:
Step II : Forming pairs that differ in just one variable also put check (v) against terms selected and finding resultant terms as below :-
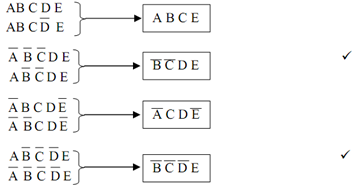
In the new terms, again find all terms that differ only in one variable as well as put a check (?) across those terms it implies that

Step III: Now, constructing final table as:
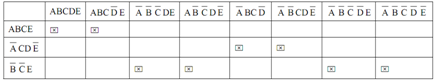
So all columns have mark 'X'. So ultimate expression is:
F (A,B,C,D,E) = ABCE + A¯C DE¯ + B¯C¯E