If the insertion violates one or more constraints, then two alternatives are available:
- Default option: - Insertion can be discarded and the reason of refusal can also be explained to the user by DBMS.
- Ask the user to resubmit, correct the data, also give the cause for rejecting the insertion.
Example:
Consider the Relation PERSON of Example :
PERSON
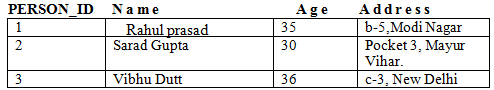
(1) Insert<1, 'Vipin', 20, 'Mayur Vihar'> into PERSON
Violated constraint: - Key constraint
Reason: - Primary key 1 already exists in PERSON.
Dealing: - DBMS could ask the user to give valid PERSON_ID value and accept the insertion if valid PERSON_ID value is given.
(2) Insert<'null', 'Anurag', 25, 'Patparganj'> into PERSON
Violated constraint: - Entity Integrity constraint
Reason: - Primary key is 'null'.
Dealing: - DBMS could ask the user to give valid PERSON_ID value and accept the insertion if valid PERSON_ID value is given.
(3) Insert<'abc', 'Suman', 25, 'IP college'> into PERSON
Violated constraint: - Domain constraint
Reason: - value of PERSON_ID is provide a string which is not valid.
(4) Insert <10, 'Anu', 25, 'Patpatganj'> into PERSON
Violated constraint: - None