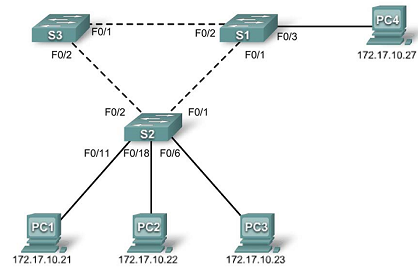
Configure the management interface address on all three switches.
S1(config)#interface vlan1
S1(config-if)#ip address 172.17.10.1 255.255.255.0
S1(config-if)#no shutdown
S2(config)#interface vlan1
S2(config-if)#ip address 172.17.10.2 255.255.255.0
S2(config-if)#no shutdown
S3(config)#interface vlan1
S3(config-if)#ip address 172.17.10.3 255.255.255.0
S3(config-if)#no shutdown
Verify that the switches are correctly configured by pinging among them. From S1, ping the management interface on S2 and S3. From S2, ping the management interface on S3.
Were the pings successful?
If not, troubleshoot the switch configurations and try again.