Question 1:
(a) (i) Radio waves are subject to several propagation problems. Name any three of them.
(ii) A Wi-Fi receiver requires a signal power of 50mW to operate correctly. Calculate the minimum required signal strength of the transmitter if the receiver is placed at a distance of 40 meters from the transmitter.
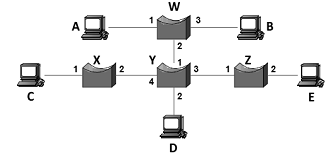
(b) Consider the arrangement of self-learning bridges shown in the figure below. Assuming all are initially empty, give the forwarding tables for each of the bridges W, X, Y and Z after the following transmissions:
Host A sends to Host C,
Host D sends to Host B,
Host C sends to Host A and
Host E sends to Host D.
(c) Give an example of a transmitted hexadecimal byte-stream in Basic Encoding Rules (BER) by using the following data type declarations and its corresponding instances:
name ::= OCTET STRING {name, "JOHN SMITH"}
active ::= BOOLEAN [0=NO, 1=YES] {inactive, 0}
number ::= INTEGER {number, 5}
(d) One method for fault tolerant servers to provide redundancy is by implementing RAID5.
(i) Explain the term redundancy.
(ii) By means of a diagram, show how data is written to four hard disks of 1TB configured as RAID5.
(iii) What is the total available space for use of the RAID5 implementation described above?