Reference no: EM131772438
Assignment 1
Overview
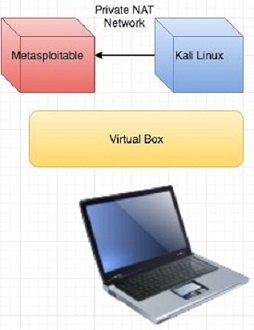
Throughout this class we will use 2 Virtual machines.
One machine will act as the attacker machine one machine will be the victim machine. This will allow us to practice in a controlled environment, if you do not follow the instructions this can lead to your account being banned on Fordham's Network.
Requirements
• The lab prep lab must have been completed before proceeding
• Ensure both network adapters on Kali and the Metasploitable virtual machines are set to a private network or host only network depending on your virtual
o This ensures the traffic never leaves your laptop
o Remember Fordham's network does have security systems which can flag your machine for malicious activity
• Metasploitable will be referred to as the target
• Document the IP addresses of each system
o Kali -
o Metasploitable -
• Only run these commands against your target machine metasploitable!
• Scanning Fordham's network will get you blocked.
• Use NMAP Commands from the presentation to complete the lab
Tasks
• Preform and document the steps outlined below
• Use the technical documentation examples as inspiration for formatting of the lab document
• Reflection should be at least one page long
Design
NMAP Basics
1. Perform a SYN Scan
2. Preform a Connect Scan
3. Perform an XMAS Tree Scan
4. Scan the system to discover operating system
5. Run a scan to show service version
6. Run a scan using the text list option
7. Run the banner script
8. Output the results to a text file
9. Grep those results to find open ports
10. Run 3 more different scans and document the results
Information Gathering
• Which ports are open on the target?
• What version of SSH is the target running?
• What version of FTP is the target running?
• What is port 5900 used for on the target?
• What OS is running on the target?
• How could you run stealth scan on the target?
• What is some other information you gathered from NMAP
Reflection
• Why would you want to detect NMAP activity on your network?
• How can NMAP be used to troubleshoot?
• Why is this tool useful from a network perspective?
• Why is this tool useful from a security perspective?
Assignment 2
Overview
The following lab will require the use of wireshark to show proficiency in network traffic analysis. Document the instructions and analysis outlined below. Complete all tasks below, provide explanation on how you identified your answers.
You should write a report responding and explain all questions and points outlined below. Screenshots should be used but sparingly and only of the relevant information not your whole desktop.
Accessing wireshark in SecOnion - Terminal wireshark
Task 1:
Instructions
• Start a wireshark capture
• Navigate to an HTTP Site (non HTTPS)
• Stop the capture
Analysis
• Create a filter for all HTTP Traffic
o What is the user agent string used?
o Was TCP or UDP used to communicate to google?
o What HTTP methods were used in the traffic?
o Use a TCP stream to view the images transferred
• Create a filter for all DNS Traffic
o Provide a screenshot of the response for the DNS request
o Was TCP or UDP used to communicate to google?
o What was the DNS server that was queried?
• Create a filter for ARP Traffic
o Why did this occur?
• Identify the three way handshake
o Show which TCP flags were used
Task 2:
Instructions
• Start a wireshark capture
• run the ping command to yahoo.com
• Stop the capture
Analysis
• Create a filter to display ICMP traffic
• What ICMP codes were used?
Task 3:
This is a capture of a client connecting to a simple HTTP webpage.
Instructions
• Open the BasicHTTPTraffic.pcap into wireshark
Analysis
• What is the OS and Web architecture used on the server?
• Follow the HTTP Stream
o What is the title of the page that was visited?
• Why doesn't this capture have any ARP Packets?
Task 4:
This is a capture of a telnet communication to a server
Instructions
• Open the telnet-raw.pcap into wireshark
• Filter on telnet
• Follow the TCP stream
Analysis
• What is the login username?
• What is the password?
• What Warning was issued?
• What OS is the server?
• When was the last login?
• What site was pinged?
• How many packets were transmitted in the ping?