Reference no: EM131406757
Hoosier Burger
Although Hoosier Burger is well recognized for its fast foods, especially the Hoosier Burger Special, plate lunches are also offered. These include such main menu items as barbecue ribs, grilled steak, meat loaf, and grilled chicken breast. The customer can choose from a variety of side items, including roasted garlic mashed potatoes, twice-baked potatoes, coleslaw, corn, baked beans, and Caesar salad. Many downtown businesses often call and place orders for Hoosier Mighty Meals. These are combination meals consisting of a selection of main menu items and three side orders. The customer can request Hoosier Mighty Meals to feed five, ten, fifteen, or twenty individuals. As a convenience to its business customers, Bob and Thelma allow business customers to charge their order. Once each month, a bill is generated and sent to those business customers who have charged their orders. Bob and Thelma have found that many of their business customers are repeat customers and often place orders for the same Hoosier Mighty Meals. Bob asks you if it is possible to track a customer's order history, and you indicate that it is indeed possible.
a. Based on the information provided in the case scenario, what entities will Hoosier Burger need to store information about?
b. For the entities identified in part a, identify a set of attributes for each entity.
c. Specify an identifier for each entity. What rules did you apply when selecting the identifier?
d. Modify Figure 7-10 to reflect the addition of these new entities. Be sure to specify the cardinalities for each relationship.
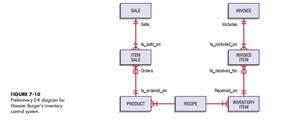
|
Do you believe that tonys family should be part of treatment
: When speaking to the juvenile justice probation officer, Tony stated that drinking and marijuana was not a serious issue and that his parents did it all the time. With this statement, the juvenile probation officer realized that this was not a one..
|
|
Is lsb watermarking robust against attacks
: Is LSB watermarking robust against attacks? If yes, explain. If not, why not? You can choose specific watermark attacks to explain your answer.
|
|
What entities are identified in the previous scenario
: Based on the case scenario and your answers to a, b, and c, prepare an entityrelationship diagram. Be sure to specify the cardinalities for each relationship.
|
|
Case of the restaurant server fired
: Consider the case of the restaurant server fired for her social media post about a customer (Section 6.3.2). What factors would you consider in deciding if the firing was reasonable? How would you compare this case with others mentioned in Section ..
|
|
What rules did you apply when selecting the identifier
: Modify Figure 7-10 to reflect the addition of these new entities. Be sure to specify the cardinalities for each relationship.
|
|
What stages of the criminal justice process are depicted
: Crime and justice are subjects that are frequently presented on television. Primetime television shows, soap operas, music videos, and cartoons often portray images of crime and criminal justice in a sensational manner or one of negativity.
|
|
Develop an outline for the final paper
: Review the Final Paper instructions in Week Five of your online course or in the "Components of Course Evaluation" section of this course guide. Develop an outline for the Final Paper, based on the topic which you chose during Week Two and your an..
|
|
Qualified job applicants for some positions
: Give some reasons why it might be difficult for companies to find qualified job applicants for some positions such as electrical engineers, network specialists, software developers, and Java programmers Should there be laws banning some kinds of h..
|
|
Current registration methods in a non-digital
: The data collected will be used for students accepted to Willowbrook, and should contain information for both the academic program and after-care programs. Keep in mind that Willowbrook conducts their current registration methods in a non-digital,..
|