Reference no: EM13762363
1. A point of synchronization between the database and the transaction log is called a(n):
before-image.
after-image.
recovery.
checkpoint.
None of these
2. An ACID transaction is one that is:
atomic.
consistent.
isolated.
durable.
All of these
3. As far as Microsoft Access is concerned, there are no:
recursive relationships.
1:1 relationships.
N:1 relationships.
1:N relationships.
N:M relationships
4. By default, when Microsoft Access creates a relationship between two tables, it creates a(n):
1:1 relationship.
N:M relationship.
1:N relationship.
recursive relationship.
association relationship.
5. The most commonly web server program is:
MySQL
Microsoft Access
Apache
every consequence of data values must originate in the definition of determinants and
keys.
php
6. Ensuring that each SQL statement independently processes consistent rows is known as:
process level consistency.
transaction level consistency.
independent consistency.
serializable consistency.
statement level consistency.
7. Given the PRODUCT and SUPPLIER entities in the figure below, which of the following would represent the correct placement of foreign keys?
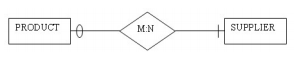
PRODUCT (ProductID, Description, Cost)SUPPLIER (SupplierID, ContactName, PhoneNumber)PRODUCT_SUPPLIER (ProductID, SupplierID)
PRODUCT (ProductID, Description, Cost)SUPPLIER (SupplierID, ContactName, PhoneNumber)PRODUCT_SUPPLIER (ProductID, SupplierID)
PRODUCT (ProductID, Description, Cost)SUPPLIER (SupplierID, ContactName, PhoneNumber)
PRODUCT (ProductID, Description, Cost, SupplierID)SUPPLIER (SupplierID, ContactName, PhoneNumber)
PRODUCT (ProductID, Description, Cost, SupplierID)SUPPLIER (SupplierID, ContactName, PhoneNumber, ProductID)
8. Given the entities PRODUCT and SUPPLIER shown in the figure below, which of the following
would represent the correct placement of foreign keys?
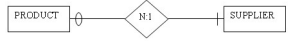
PRODUCT (ProductID, Description, Cost)SUPPLIER (SupplierID, ContactName, PhoneNumber, ProductID)
PRODUCT (ProductID, Description, Cost, SupplierID)SUPPLIER (SupplierID, ContactName, PhoneNumber)
PRODUCT (ProductID, Description, Cost)SUPPLIER (SupplierID, ContactName, PhoneNumber)
PRODUCT (ProductID, Description, Cost, SupplierID)SUPPLIER (SupplierID, ContactName, PhoneNumber, ProductID)
PRODUCT (ProductID, Description, Cost, ContactName)SUPPLIER (SupplierID, ContactName, PhoneNumber)
9. Given the generic relation: GENERIC (PKey1, PKey2, Attribute1, Attribute2, Attribute3), and the functional dependencies: (PKey1, PKey2) → Attribute1 and PKey2 → (Attribute2, Attribute3), which of the following is true?
GENERIC is not fully normalized.
PKey1 is a determinant.
PKey2 is a candidate key.
GENERIC is in DK/NF.
All of these
10. Given TABLE_A (Attribute1, Attribute2, Attribute3) and TABLE_B (Attribute4, Attribute5, Attribute6) shown in the figure below, which of the following would display the correct placement of foreign keys in the relational model?
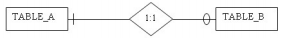
TABLE _A (Attribute1, Attribute2, Attribute3, Attribute4, Attribute5)TABLE _B (Attribute4, Attribute5, Attribute6)
TABLE _A (Attribute1, Attribute2, Attribute3, Attribute6)TABLE _B (Attribute4, Attribute5, Attribute6)
TABLE _A (Attribute1, Attribute2, Attribute3)TABLE _B (Attribute4, Attribute5, Attribute6)
TABLE_A (Attribute1, Attribute2, Attribute3)TABLE _B (Attribute4, Attribute5, Attribute6, Attribute1)
TABLE _A (Attribute1, Attribute2, Attribute3, Attribute4)TABLE _B (Attribute4, Attribute5, Attribute6, Attribute1)
11. Preventing multiple applications from obtaining copies of the same record when the record is about to changed is called:
serialized reading.
lost updating.
concurrent processing.
resource locking.
block factoring.
12. SQL statements can be run individually or as part of a related group of SQL statements known as a(n):
Commandset.
Script.
Scriptset.
Resultset.
Result.
13. The fundamental rule of normalization can be stated as:
every table must meet the definition of a relation.
every determinant must be a candidate key.
every constraint must be a determinant.
every key must be a candidate key.
every domain must be a logical consequence of the constraints.
14. The purpose of concurrency control is to:
ensure that one user's work does not interfere with another's.
ensure that triggers do not invoke stored procedures.
ensure that each form has a corresponding report.
ensure that ASPs do not duplicate JSPs.
ensure that stored procedures do not invoke triggers.
15. The recovery technique in which the database is returned to a known state and then all valid transactions are reapplied to the database is known as:
checkpointing.
rollforward.
rollback.
reprocessing.
transaction logging.
16. The term DBA refers to the:
data business administrator.
data business auditor.
database accessor.
database auditor.
database administrator.
17. To create a 1:1 relationship between two tables in Microsoft Access:
the Indexed property of the foreign key column must be set to Yes (No Duplicates).
the Indexed property of the foreign key column must be set to No.
the Data Type of the foreign key column must be set to AutoNumber.
the Smart Tag property of the foreign key column must be set to Foreign Key.
the Indexed property of the foreign key column must be set to Yes (Duplicates OK).
18. What concurrent processing problem occurs when a transaction rereads data and finds new rows that were inserted by a diferent transaction since the prior read?
Phantom reads
Unlocked reads
Serialized reads
Nonrepeatable reads
Dirty reads
19. What is the least restrictive isolation level that will prevent dirty reads?
Read Committed
Read Uncommitted
Atomic Read
Repeatable Read
Serializable
20. What is the least restrictive isolation level that will prevent nonrepeatable reads?
Repeatable Read
Read Uncommitted
Read Committed
Serializable
Atomic Read
21. What is the least restrictive isolation level that will prevent phantom read problems?
Read Committed
Repeatable Read
Atomic Read
Serializable
Read Uncommitted
22. What relationship pattern is illustrated in the following schema?
VehicleID in CAR must exist in VehicleID in
VEHICLE VehicleID in TRUCK must exist in VehicleID in VEHICLE
Strong entity relationship
Intersection relationship
Recursive relationship
Supertype/subtype relationship
Association relationship
23. The most commonly used language to manipulate data in a database is:
Ruby
SQL
C++
Microsoft Access
24. When a transaction functions in such a way that either all of the transaction actions are completed or none of them will be, the transaction is said to be:
logical.
atomic.
consistent.
locked.
isolated.
25. When distributed databases create copies of the database on diferent servers, thisis known as:
replication
partitioning.
disbursing.
distributed two-phase locking.
None of these
26. Whether a lock applies to data at the record level, page level, table level, or database level is referred to as:
lock exclusivity.
lock phasing.
lock granularity.
serializable locking.
lock sharing.
27. The most commonly used database program in websites is:
MySQL
PHP
Oracle
DK/NF
Microsoft SQL Server 2
28. Which normal form is defined as any table meeting the definition of a relation?
DK/NF
4NF
BCNF
1NF
2N
29. What programming language is most often used to pass user input from a web interface to a database?
Access
PHP
Oracle
Java
30. Which of the following is not true of database recovery through reprocessing?
Reprocessing makes use of a database save.
Reprocessing takes the same amount of time as did processing in the first place.
Reprocessing will always return the database to its exact previous state.
Reprocessing requires a record of all transactions since the last time the database was saved.
All of these are true of reprocessing.
31. Which of the following is the correct technique for representing a 1:N relationship in the relational model?
The key of either relation can be placed into the other relation.
The key of the entity on the one side is placed into the relation for the entity on the many side.
The key of the child is placed into the relation of the parent.
The key of the entity on the many side is placed into the relation for the entity on the one side.
An intersection relation is created and the keys from both parent entities are placed as keys in the intersection relation
32. Which of the following is the correct technique for representing a M:N relationship using the relational model?
An intersection relation is created and the key of either entity is placed as a key in both the intersection relation and in the other relation.
An intersection relation is created with a surrogate key, which is placed in each of the parent entities.
An intersection relation is created and the keys of both parent entities are placed as a composite key in the intersection relation.
The key from either relation is placed as a foreign key in the other relation.
None of these
33. Which of the following is the first step in representing entities using the relational model?
Define a primary key.
Determine identifiers.
Determine foreign keys.
Examine the entity against normalization criteria.
Define a table for each entity.
34. Which of the following is true about a shared lock?
It is more restrictive than an implicit lock.
It locks the item from all access.
It allows only two transactions to update a record simultaneously.
It allows reads to the locked item.
It must use a two-phase locking scheme.
35. Which of the following is true about representing a weak entity with the relational model?
If the weak entity is ID-dependent, the key of the parent entity must be part of the key of the weak entity.
If the weak entity is ID-dependent, the key of the weak entity must be part of the key of the parent entity.
If the parent entity is existence-dependent, then the minimum cardinality of the weak entity is zero.
If the strong entity has a minimum cardinality of 1, the key of the weak entity must be part of the strong entity.
If the weak entity is existence-dependent, the key of the parent must be part of the key of the weak entity.
36. Which of the following is true when representing a 1:1 binary relationship using the relational model?
The key of the entity with the highest minimum cardinality must be placed in the other entity as a foreign key.
The key of either entity is placed in the other as a foreign key.
Both entities must have the same primary key.
The key of each entity must be placed in the other as a foreign key.
The key of the entity with the most attributes must be placed in the other entity as a foreign key.
37. Which of the following is not a means of processing databases?
Internet applications using ASP
Internet applications using JSP
Applications invoking stored procedures
Programs coded in C#
All of these are means of processing a database.
38. What language is most often used to pass SQL query results to a user's web interface?
Perl
Python
Linux
php
39. Which of the following would be a reason to denormalize a relation?
Relax security
Lack of design time
End user preference
Improve performance
None of these
40. Which type of lock assumes that no conflicts will occur?
Optimistic locks
Explicit locks
Shared locks
Granular locks
Open locks