Reference no: EM131293417
For the double semicircle task in Problem, set sep = -5 and generate 2, 000 examples.
(a) What will happen if you run P LA on those examples?
(b) Run the pocket algorithm for 100, 000 iterations and plot Ein versus the iteration number t.
(c) Plot the data and the final hypothesis in part (b).
(d) Use the linear regression algorithm to obtain the weights w, and compare this result with the pocket algorithm in terms of computation time and quality of the solution.
(e) Repeat (b) - (d) with a 3rd order polynomial feature transform.
Problem
Consider the double semi-circle "toy" learning task below.
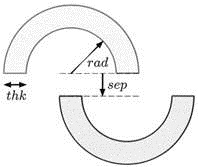
There are two semi circles of width the k with inner radius rad, separated by sep as shown (red is -1 and blue is +1). The center of the top semicircle is aligned with the middle of the edge of the bottom semicircle. This task is linearly separable when sep 2: 0, and not so for sep k = 5 and sep = 5. Then, generate 2, 000 examples uniformly, which means you will have a pproximately 1, 000 exam ples for each class.
(a) Run the PLA starting from w = 0 until it converges. P lot the data and the final hypothesis.
(b) Repeat part (a) using the linear regression (for classification) to obtain w. Explain your observations.
|
Decreases in gross domestic product
: From you reading, it is clear that contractionary monetary policy decreases the money supply in an economy. When there is a decline in money supply, it will contribute to decreases in Gross Domestic Product.
|
|
Describe the ethical issues faced by defense attorneys
: Describe the ethical issues faced by defense attorneys and prosecutors.
|
|
Main determinants of aggregate supply
: It has been asserted that the main determinants of aggregate supply can be grouped into four: resource quantity (e.g., labor, capital, land, and entrepreneurship), resource quality or productivity, and resource price.
|
|
Present your business idea to a group of investors
: You have been working on your business idea and are ready to present your idea to a group of investors. You are going to present your business idea using a PowerPoint presentation which includes embedded charts and tables.
|
|
Plot the data and the final hypothesis
: What will happen if you run P LA on those examples?- Run the pocket algorithm for 100, 000 iterations and plot Ein versus the iteration number t.
|
|
Show your ability to provide reasoning for your response
: Please note that this is an MBA course so you must show and demonstrate your ability to provide reasoning for your response to discussion questions.
|
|
What is the present worth of the total
: What is the present worth of the total 20 payments, occurring at the end of every four months (i.e. the first payment is in four months), which are $400, $500, $600, increasing by a fixed sum. Interest is 12% nominal per year, compounded monthly.
|
|
Explain wage differential between three jobs in organization
: List the main factors that may help to explain the wage differential between three jobs in an organization with which you are familiar. How have the major labor relations laws helped or hindered the development of unions?
|
|
Impact of trump and obama economic policies
: What is the impact of trump and Obama's economic policies on the business opportunities for US based global firms, such as Apple, IBM etc?
|