Reference no: EM131311269 , Length:
Part-1
Given the following design for a money transfer protocol which utilizes public key cryptography to assure confidentiality and authenticity of the transmission.
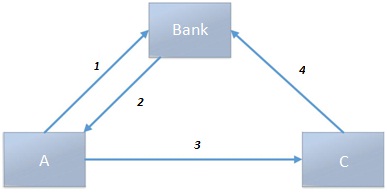
Issuing a Check:
1. Payee (A) will contact the bank requesting the issuance of $ amount check made payable to (B).
2. Bank responds by sending the payee a check receipt CR, where:
CR = RSA( PuA , check )
check = RSA( PuC , token )
token = AES128( KeyBank , amount )
3. Payee (A) receives the check receipt from the bank, extract the check from it and pass it to the receiver (C).
4. The receiver extracts the token from the check and pass it to the bank encrypted with its own private key to collect the money.
From C to Bank: RSA( PrC , token )
Given the following information about A, C, and the Bank:
For A:
Modulus (n):
C18A039606DE728621672C5CB4CC5F03FFD3D7B918D9B614CDA3B071CF458FC2AFE92CD8B4847976A3DD65C61
25C770BE59286BE1D67C638012C542FD91280F5269A8E740C352D965506E140C0ACB97941279FEA36C3044685FB
2DC60BCF95D491FAE881F1A9324691F22079263065A3A788C8037C9A2DA6DA050FA7AE784999
Public Exp. (e): 010001
Private Exp.(d):
35359E9AC6B4ADC3D6B728E92C03EC338B4850CCE0DA2A4739EA40FE693FF4B04FF0C995A2BBB1313F08058D19
4B36A79CAC56433A8E675ECA63C7998812A0454B2DFED7D485DA88D7D029F3431D753E7ADD4DD92C2C2B5338
67B0CED8CE2A22E5273DF1D4D88198FC9857C18FC281FCE1BE6F5F0770EB63284EA1704D207A49
For C:
Modulus (n):
E021A9DFBD816E2451A5504898FDCE92B99E7CC54F09CBFF1443736B0C6E1E8F271A93CDA752B7070F0E0AB243
B391000F086526ABD9D3E4F92E4D821EC5CD8BEE797F5BAA7B54AC1AE74F233263C9723B6125980FBBB8142C6A
9F86A0A2DBB966280279EE7197FFF421AFB438FDA598F8A22551634EADB50B1E86B76BC6A9A3
Public Exp. (e): 010001
Private Exp.(d):
76DC035D5EFF3BACD10B8D36E2C37E803B25BC5F5A9A046FE28C1EB23F664A987A11531EB5C45CC1C68F18C70E
B6348846709A4BD6C8EEE137F00134A72318EC455B5E74709306312B00AE2F51FB548F6FAC811C32A99E4B361DB
6C2727F00D317286F5FBE5D9830BA6EA19F68A4BFB5EC80EF2E2948FC0702B04D448EB0EAB1
For the Bank:
AES128 Key: C1D0F8FB4958670DBA40AB1F3752EF0D
Calculate the messages sent in steps 1 to 4 if A is sending $ amount equals to your NYIT ID to C.
Part-2
Propose an electronic cash transfer system (similar to Bitcoin) that is completely decentralized. Illustrate how funds transfer can take place. Show the different system components and the cryptographic techniques used to implement your design.
Perform a risk assessment on your design and compare it to existing eCash transfer systems.
|
Major substantive objection to general equilibrium theory
: What is Hayek's major substantive objection to general equilibrium theory?
|
|
Percentage points of the actual proportion
: Suppose that 60 percent of the voters in a particular region support a candidate. Find the probability that a sample of 1,000 voters would yield a sample proportion in favor of the candidate within 3 percentage points of the actual proportion.
|
|
Explain the stages and domains of development
: Based on your observations, explain the stages and domains of development, including physical and motor development, social-emotional development, self-help development, cognitive development, and language development.
|
|
Calculate the t matrix for dct
: Using one-dimensional DCT encoding, calculate the M matrix from the following three p matrices (which are given as row matrices but need to be considered as column matrices). Interpret the result.
|
|
Perform a risk assessment on your design
: Perform a risk assessment on your design and compare it to existing eCash transfer systems - Propose an electronic cash transfer system (similar to Bitcoin) that is completely decentralized. Illustrate how funds transfer can take place.
|
|
Evaluate the success of it systems
: What sort of effectiveness metrics would the health care industry likely use to evaluate the success of IT systems?
|
|
Happening to the total revenue
: Now, starting with the price of $6 and working down the demand curve $1 at a time, explain what is happening to the total revenue at each price and why. You need to relate the TR back to the Ed formula and explain.
|
|
What is the value of t in this case
: In one-dimensional DCT, if N = 1, the matrix transformation is changed to simple multiplication. In other words, M = T × p, in which T, p, and M are numbers (scalar value) instead of matrices. What is the value of T in this case?
|
|
Have you suffered any loss of weight
: When were you diagnosed with diabetes? What symptoms did you experience before you were diagnosed with diabetes? How many times do you need to pee on a daily basis?
|