Reference no: EM131113884
Questions 1 -5 refer to the following scenario.
Suppose you are a manufacturer of product XYZ, which is composed of parts X, Y, and Z. Each time a new product is created, it must be added to the product inventory, using the PROD_QOH in a table named PRODUCT. And each time the product XYZ is created, the parts inventory, using PART_QOH in a table named PART, must be reduced by one each of parts X, Y, and Z. The sample database contents are shown below:
The Database for Problem 1-5
Table name: PRODUCT Table name: PART
|
PROD_CODE
|
PROD_QOH
|
|
PART_CODE
|
PART_QOH
|
|
XYZ
|
950
|
|
X
|
395
|
|
|
|
|
Y
|
390
|
|
|
|
|
Z
|
405
|
Given that information, answer Questions 1 through 5.
1. How many database requests can you identify for an inventory update for both PRODUCT and PART?
2. Using SQL, write each database request you identified in problem 1.
3. Write the complete transaction(s).
4. Write the transaction log, using tables below, as your template.
We assume that product ‘XYZ' has a PROD_QOH = 950 at the start of the transaction and that the transaction is representing the addition of 1 new product. We also assume that PART components "X", "Y" and "Z" have a PROD_QOH equal to 395, 390, and 405 respectively.
|
TRL ID
|
TRX NUM
|
PREV PTR
|
NEXT PTR
|
OPERATION
|
TABLE
|
ROW ID
|
ATTRIBUTE
|
BEFORE VALUE
|
AFTER VALUE
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
5. Using the transaction log you created in Step 4, trace its use in database recovery.
6. Describe the three most common concurrent transaction execution problems. Explain how concurrency control can be used to avoid those problems.
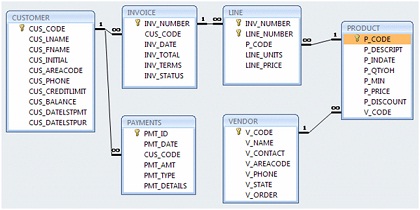
Questions 7 -10 refer the following scenario as represented in the CGS2541 Project 9 ABC.mdb Access Database. The relational diagram shown below represents the main entities for ABC's database. Note the following important characteristics:
• A customer may make many purchases, each one represented by an invoice.
- The CUS_BALANCE is updated with each credit purchase or payment and represents the amount the customer owes.
- The CUS_BALANCE is increased (+) with every credit purchase and decreased (-) with every customer payment.
- The date of last purchase is updated with each new purchase made by the customer.
- The date of last payment is updated with each new payment made by the customer.
• An invoice represents a product purchase by a customer.
- An INVOICE can have many invoice LINEs, one for each product purchased.
- The INV_TOTAL represents the total cost of invoice including taxes.
- The INV_TERMS can be "30," "60," or "90" (representing the number of days of credit) or "CASH," "CHECK," or "CC."
- The invoice status can be "OPEN," "PAID," or "CANCEL."
• A product's quantity on hand (P_QTYOH) is updated (decreased) with each product sale.
• A customer may make many payments. The payment type (PMT_TYPE) can be one of the following:
- "CASH" for cash payments.
- "CHECK" for check payments
- "CC" for credit card payments
• The payment details (PMT_DETAILS) are used to record data about check or credit card payments:
- The bank, account number, and check number for check payments
- The issuer, credit card number, and expiration date for credit card payments.
Note: Not all entities and attributes are represented in this example. Use only the attributes indicated.
FIGURE P10.6 The ABC Markets Relational Diagram
7. Using this database, write the SQL code to represent the following transaction. Use BEGIN TRANSACTION and COMMIT to group the SQL statements in logical transactions.On March 28, 2016, customer ‘80200' makes a credit purchase (30 days) of one unit of product ‘1546-QQ2' with a unit price of $30.00; the tax rate is 8 percent. The invoice number is 9910, and this invoice has only one product line.
8. Create a simple transaction log, in the table below, to represent the actions of the previous transaction in #7.
|
TRL ID
|
TRX NUM
|
PREV PTR
|
NEXT PTR
|
OPERATION
|
TABLE
|
ROW ID
|
ATTRIBUTE
|
BEFORE VALUE
|
AFTER VALUE
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
9. Assuming that pessimistic locking is being used, but the two-phase locking protocol is not, create a chronological list of the locking, unlocking, and data manipulation activities that would occur during the complete processing of the transaction described in Problem 7.
|
Time
|
Action
|
|
1
|
|
|
2
|
|
|
3
|
|
|
4
|
|
|
5
|
|
|
6
|
|
|
7
|
|
|
8
|
|
|
9
|
|
|
10
|
|
|
11
|
|
|
12
|
|
Cust
10. Assuming that pessimistic locking with the two-phase locking protocol is being used, create a chronological list of the locking, unlocking, and data manipulation activities that would occur during the complete processing of the transaction described in Problem 7.
|
Time
|
Action
|
|
1
|
|
|
2
|
|
|
3
|
|
|
4
|
|
|
5
|
|
|
6
|
|
|
7
|
|
|
8
|
|
|
9
|
|
|
10
|
|
|
11
|
|
|
12
|
|