Reference no: EM13313401
Scenario: Stella changes banks following her troubles with SHB. At her new bank, Ultimate Security Trust (UST), RSA is used as the cryptographic system. She creates a key pair and supplies Fiona, an officer of UST who will handle her account, with her public key {eA, nA}, securing her private key {dA, nA} on a floppy disk which she keeps locked in a wall safe at her home. In turn, Fiona gives Stella access to a key server maintained by UST so that she can readily obtain Fiona's current public key {eF, nF} whenever she needs to communicate securely with Fiona.
Things are fine for several months until Stella sends Fiona a message m asking about current interest rates on Certificates of Deposit issued by UST. As shown below, she enciphers the message first, and then signs it:
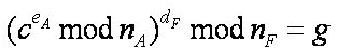

A few days later, Stella received a statement that shows a debit of $1,000,000 from her account. On inquiring, she was told that Fiona transferred the money out of Stella's account into an account of her own in a bank on the Caribbean island of Nevis. When reached via long distance in Nevis, Fiona produced a message g from Stella saying: "Thanks for your excellent service, Fiona. Please transfer $1,000,000 from my account to yours as a token of my esteem and appreciation. -Signed, Stella."
Stella files suit against Fiona, UST and the government of the Nevis, claiming that the message was a forgery sent by Fiona herself, asking for triple damages for pain and suffering. Fiona has responded by claiming that all procedures were followed properly and that Stella is filing a nuisance suit.
You have been employed by UST as a cryptographic expert to assist in the investigation of this matter and help them decide what to do with Stella issue. You obtain Fiona's private key from the UST server, and the cipher text c, and calculate
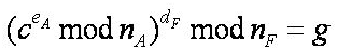
Your report to the UST Board of Directors should address the following issues:
- From the facts as presented what can be determined about Stella's intentions to make Fiona a gift of $1,000,000?
- What is the significance of Nevis Island?
- What is the significance of Stella's message to Fiona asking for interest rates?
- Assuming UST wishes to continue using RSA as its cryptographic system, what UST and Stella could have done to protect against this controversy arising?
Your report should clearly address these issues including recommendation for the Stella's suit, with sufficient detail and background to allow the Board of Directors who are cryptographically challenged to understand the issues involved and formulate plans for how to approach the immediate issue with Stella, and to continue business in the future, assuming that they want to continue using only RSA. Assume that the directors do not know what RSA is and/or how it works.