Reference no: EM132961562
Networking Technologies Assignment
Objectives
The objective of this assignment is to assess your understanding of fundamental networking structure and network design concepts, and your ability to apply them to practical exercises using a tool (Packet Tracer).
Learning Outcome 1: Analyse and evaluate network technologies and services using a layered approach and network standards.
Learning Outcome 2: Formulate and analyse a network design for small medium enterprise networks.
Preparation
1) This assignment requires students to produce a Panopto video based on task instructions below. This assignment requires video recording equipment such as a notebook equipped with a camera, as well as the software Panopto (in Blackboard). If required, you can borrow a laptop from the library.
2) You should be familiar with Panopto in Blackboard and Packet Tracer for this assignment. It is recommended that you carefully follow the Panopto instructions when submitting your work. It is your responsibility to submit a video and a Packet Tracer (pkt) file correctly according to the instructions. Make sure you select the ‘Panopto Student Video Submission' option as shown below. Otherwise, it will not be successfully submitted.
IMPORTANT: If you submit your video via the wrong option it may delay the marking of your assessment and/or lead to late penalties. It is the responsibility of students to watch these video instructions and to follow them closely. You can edit your submission multiple times prior to the due date.
3) Practice recording a few times to keep within the time limit, and use the rubric as a guide, as it will be used for grading. Check here to learn how merge videos if necessary. Visit the Panopto for Students intranet site for more resources, and watch the video in the submission folder paying particular attention to the right Mashup tool for submission.
Requirements:
Watch this video before submitting your assignment
You will need to show footage of yourself completing each task, as well as footage of yourself speaking to the camera about each task.
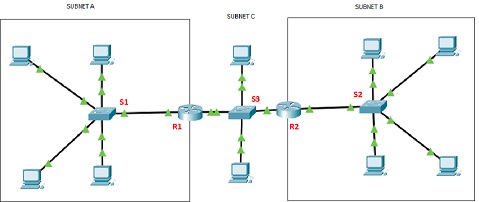
Figure 1 Network topology.
Task 1 Network Design and Plan
Design and configure routers and hosts (but switches) in the network by allocating each IP addresses in an appropriate and minimal range (to maximise the spare ranges for future use) as shown in Figure 1 using Packet Tracer, and verify the connectivity fully works across the network including inter and intra networks.
Notes:
1. Use ‘ping' to verify connectivity ‘successful' status
2. Display names and IP addresses of devices and interfaces on the Packet Tracer screen
3. Use/design smallest subnet mask for each network where possible
4. Show the subnetting scheme in a single page in your presentation
5. Check ‘no auto-summary' command, which will be required to configure routing protocol such as RIP
and EIGRP
Task 2 Layer 2 Implementation and Analysis
In Subnet A, redesign and configure the network to allocate VLAN10 and VLAN 20 for 2 hosts by allocating each IP addresses in an appropriate range. Check connectivity within the same and different VLANs.
Demonstrate how Layer 2 and Layer 3 work differently by enabling and disabling the R1 interface, and analyse the results and explain why it was a ‘success' or ‘failure'.
Task 3 Layer 3 Evaluation
In Subnet B, clear the ARP table of devices, and ping from a host in Subnet B to a host in Subnet C. Evaluate and analyse how Layer 2 and Layer 3 addresses (source and destination) are allocated in each network's ingress and egress interfaces. For example, what address is and is not changed at the router interfaces with Subnet A and C? Explain why and justify your answers.
Attachment:- Networking Technologies.rar