Reference no: EM131120170
The primary purpose of this first Lab Assignment is for you to familiarize yourself with the environment that we will use this semester for exploring network security issues.
The tasks you should perform are
- Install VirtualBox on a machine that you own or have access to
- Import a Tiny Core Linux virtual machine (VM) that I provide to you
- In the VM, set up your terminal prompts with your name, and execute a few basic commands to make sure everything works
- Perform several simple "packet extractions" using tcpdump
To complete this assignment, you will upload (this is repeated at the bottom of the assignment)
- A snapshot graphic showing your Tiny Core Linux running with two terminals, one of them running tcpdump, and the other running a telnet client.
- The tcpdump files, port23.txt and port22.txt, that you will create.
- A written explanation of your understanding of the various flags and commands used to run tcpdump
- A written explanation of your attempts to telnet and/or ssh to the Tiny Core Linux guest OS from the host computer, or another computer on the same network.
Installation and initial familiarity with the software
I have prepared a document that provides an overview of the installation. It is available on the Blackboard assignment page, as VirtualBox Install and Familiarization.
This is not a comprehensive document, and not all details are covered, but you should use it as guidance in the installation and usage of the Tiny Core Linux VM. If you run into problems that you are unable to solve, please use the Blackboard Discussion forum to ask the questions publicly for the benefit of everybody. Likewise, please feel free to contribute any answers to questions that other students may ask.
You should install VirtualBox and the Tiny Core Linux VM as outlined in the VirtualBox Install and Familiarization document mentioned above before proceeding to the next step.
Be sure that you set up (as described in the setup instructions) the terminal command line prompt so that it has your name in it. It is important that your name is visible in at least some of your screen shots your goal should be to show me that this is YOUR work, and not copied from somebody else.
Initial familiarity with tcpdump
Your primary goals, in terms of assignment submission, are
- to provide me with a graphic that shows you using tcpdump in one window and telnet in another, as well as the text files you created from running tcpdump
- to explain your understanding of the tcpdump utility and the command line flags that I have asked you to use.
- to explain to me whether you are able to telnet and/or ssh into your guest Tiny Core Linux OS from the host computer, or from another computer on the same network. If you have problems doing this, please explain in detail why you are not able to. You will not lose points if you are unable to telnet and/or ssh into the guest Tiny Core Linux OS from outside, but you are required to explain what you tried, and why it didn't work.
These are the basic actions you should take to start running and testing tcpdump. You don't have to do it exactly as I specify these are just provided as guidance.
In your Tiny Core Linux guest virtual machine (VM)
- Open a terminal
- Using nano or vi, create a simple text file with 23 lines of text in it (something that you will recognize later). In this text, you should include your name, for identification purposes.
- Save it, and make sure you can "cat" it (e.g. cat myfile.txt)
- Run tcpdump so that it captures telnet packets on the lo interface (this is the "loopback" interface, and whenever you connect to localhost, the traffic passes through this interface, locally, rather than one of the ethernet interfaces). Note that the telnet server listens for traffic on Port 23.
- Run tcpdump as follows, and leave it running
sudo tcpdump -l -i lo -A port 23 | tee port23.txt
- As part of the assignment, you should do a little research on tcpdump, and anything else you don't understand in the above command, and fully explain what this command does. In other words, explain sudo, tcpdump, and what all of the command line flags mean
- Open another terminal
- In the new terminal, telnet to the localhost (the userid is tc, and there is no password). Watch what happens in your tcpdump window as you do so. The output can be confusing, but see if you can spot your keystrokes in those packets. Keep in mind that telnet sends one packet per keystroke, then echoes it back to the client for display
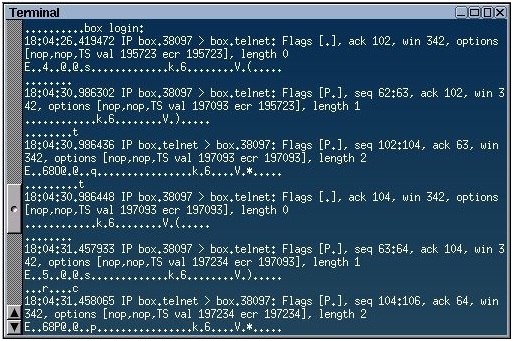
In the following example, you can see my output from the tcpdump command I had to scroll back up the window, but you can see the login prompt at the top, and if you look close, you can see the ......t and the .......c that I typed in.
- When logged in, do a directory listing (ls) and, again, see if you can spot your keystrokes, plus the response to your ls command in the window that displays the tcpdump packets.
- cat the file that you created earlier. Verify that you can see your keystrokes in there, plus the expected output from the cat command.
- exit from telnet (just type exit in that terminal)
- telnet localhost again, using a nonexistent userid (e.g. mcis), then enter a long password with a pattern that you'll be able to recognize in the tcpdump packet output(e.g. abcdefghijklmonp....). Verify that you can see the individual characters somewhere in the packets in other words, you can sniff passwords. While you are doing this, take a snapshot of the Tiny Core Linux screen and save the PNG file for upload to Blackboard.
- exit from telnet again and stop tcpdump (CTRLC). The tcpdump output should be present in the file port23.txt, and you may use this to review your session.
- Now repeat the same steps with ssh (you will need to modify the command, because ssh listens on Port 22)
• Start tcpdump to listen for ssh messages
• ssh to localhost (simply, ssh localhost)
• perform the ls and cat operations on the test file, and this time you should note that everything is encrypted. You should not see any evidence of what you are doing.
• Exit from ssh, and then try to login with a bad userid (e.g. ssh mcis@localhost) and verify that you can't see any login/password data in tcpdump it should all be encrypted.
• Exit ssh and tcpdump, and note that your session output has been saved in the file that you specified.
To complete this assignment, you should turn in a single PDF or Word (or OpenOffice) document which contains the following Please, no ZIP files, no tar files, just a single PDF or Word/OpenOffice file.
- An explanation of your experiences in the set up for VirtualBox and TinyCore Linux. Was it easy or hard• Did you have any problems• If so, describe them.
- A snapshot graphic showing your Tiny Core Linux running with two terminals, one of them running tcpdump, and the other running a telnet client. Be sure that your name is clearly visible in the prompt. Here is an example from my own session:

- A written explanation of your understanding of the various flags and commands used to run tcpdump.