Reference no: EM131224060
Question 1: Explain about Snort Rules, create rules and test the created rules.
Question 2: Kerberos Authentication Protocol
You are required to do personal research to complete the following questions regarding this topic:
To answer these questions, you should consult reference materials from other texts and the Internet. You are required to reference these sources - DO NOT DIRECTLY COPY material from them - i.e. use your own words.
A. Give your general description of the Kerberos authentication protocol.
B. Explain the term: Authenticator used in the Kerberos authentication protocol.
C. In the Kerberos authentication protocol, there are 3 basic roles: client, server and Key Distribution Centre (KDC). Give your description of each of them.
D. By explaining the term: Session Ticket, describe how a session key is created by KDC, and distributed to the client and the server
E. Describe the mutual authentication procedure between the client and the server after the client obtains the session ticket
Question 3: Wireless Protocols
To answer some of these questions, you should consult reference materials from other texts and the Internet. You are required to reference these sources - DO NOT DIRECTLY COPY material from them - i.e. use your own words.
You are required to do personal research to complete the following questions regarding this topic:
A. Describe 802.1x authentication and the steps that when a wireless client connects to a network using RADIUS server for authentication.
B. Explain the PEAP protocol - how does it differs from EAP and what EAP deficiency does it address?
C. What makes a brute-force attack both particularly difficult and potentially easy on a wireless network using AES/CCMP encryption and 802.1x authentication? Hint: What do you need to know in order to attempt the attack?
D. Assume an office wireless network was only configured with WPA2-AES encryption (i.e. no additional authentication standards). What problems would this cause?
E. Assume an office wireless network was only configured with 802.1x authentication (i.e. no additional encryption). What problems would this cause?
Question 4: Steganography Exercise
This exercise requires you to use Steganography to embed secret text into a graphic file and also to embed a secret watermark into a second graphic file. To accomplish these tasks you are to download a copy of OpenStego from the internet.You will also need to download the two graphic files cqu_logo.png andBundaberg.jpg from the Moodle site.
a) Data Hiding in a graphic file
b) Watermarking a second graphic file
Question 5
You are the Chief Information security Officer (CISO) of a small medium sized - accounting Services Company. In the last few weeks, senior staff have been complaining that some confidential information has been disclosed via email without any authorisation. You are approached by the Chief Information Officer (CIO) to discuss the issue and see the most appropriate way to tackle this problem. You suspect that some of the employees might be using their technical skills to access sensitive information either from the mail serversor during transmission. To counteract this malpractice, you suggest the CIO the implementation of encryption. Before you actually implement the system, you want to conduct a pilot using the GNU Privacy Guard (GPG) software.
The pilot requires that you install GNU Privacy Guard (GPG) software onto your own computer and complete the following activities.
Note: The GNU Privacy Guard is available for free download from https://www.gnupg.org/ and "APractical Introduction to GNU Privacy Guard in Windows" by Brendan Kidwell is available at https://www.glump.net/howto/gpg_intro
After installing GPG software onto your own computer, complete the following tasks:
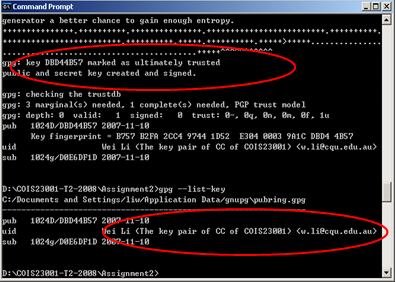
1. Generate your own key-pair by using GPG software and do not create a pass-phrase for your private key (in a real world this is not a good practice. Just for the sake of this assignment, do not create a pass-phrase). You need to use screen-shots to show that you have successfully completed this task. A valid screen-shot is similar to the one shown in Figure 1. Pay attention to the red circles, which demonstrate the success of key pair generation
Figure Key Pair Creation
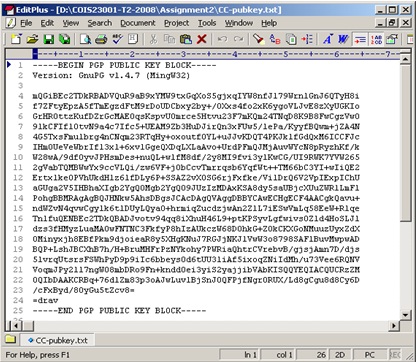
2. Export your public key and paste it into your assignment document. You need to use two screen-shots to show that you have successfully completed this task. One screen-shot is to show the use of gpg command and the other is to show the exported public key. For example, the screen-shot in Figure 2, shows a public key, which is exported into the file: CC-pubkey.txt.
3. Explain the steps how to import your Lecturer's public key from the key-server https://pgp.mit.edu (your lecturer created a public key and stored it at the MIT PGP Public Key Server). Include in the assignment document the gpg command line, individual options you used and their meaning. As above, use screenshots of website interactions, with accompanying explanations of the screenshots to explain the steps how to import your Lecturer's public key from the key-server https://pgp.mit.edu.
4. Create an ASCII text file to store your full-name, your student number, and your student CQU email address (please do not use any other email address). Then using your lecturer's public key, encrypt this text file. The resulting file should also be ASCII armored so that it is readable once decrypted by your lecturer / tutor. Failure to do so will result in loss of marks. Submit the resulting encrypted file along with your assignment solutions document (word document) via the online submission system and following the naming convention given above.