Reference no: EM133316
Question 1
Give details for the following terms as used in cryptography:
(a) Block cipher,
(b) Primitive root,
(c) Confusion,
(d) Diffusion,
(e) Digital signature.
Question 2
(a) You have interrupted a message encrypted by a general Caesar cipher. You know that the ciphertext "MUUJ CUXQ" ends with 'K'. Find the key and decrypt the message.
(b) The single letters in a 26-letter alphabet consist of A to Z, where A to Z have numerical equivalents 0 to 25.

Question 3
A string of ciphertext was enciphered using an affine transformation of single letters in a 26-letter alphabet consisting of A to Z, where A to Z had numerical equivalents 0 to 25. A frequency analysis reveals that the the first and second most common letters of this ciphertext are K and D, respectively. Suppose that the first and second most ordinary letters in an English language text written in this 26-letter alphabet are E and T, respectively. Discover the deciphering transformation.
Question 4
(a) Make the Playfair matrix (5 × 5) using the keyword "cryptosystem" .
(b) Therefore, encrypt the message "mortal" .
(c) In addition with, decrypt the message "IU NI QE IB XN" .
Question 5
(a) Depict the dissimilarity between Conventional Symmetric-Key Encryption and Public-Key Encryption in terms of security and steps/algorithms involved.
(b) In a public-key system using RSA, you intercept the ciphertext C = 10 sent to a user whose public key is e = 5, n = 35. What is the plain text M?
Question 6
(a) The Matlab code (fastexp m-file) which uses fast exponentiation (Repeated Squaring Method) to Compute x = ak mod n is given underneath:
function [x]=fastexp(a,k,n)
i=0;
remainder=k;
array=[];
expon=[];
x=1;
while remainder>0
test=remainder-(2 ∧ i);
if test> (2 ∧ i)
i=i+1
else
array=[array i];
remainder=remainder-(2 ∧ i);
i=0;
end
end
expon=zeros(1,array(1)+1);
expon(1)=mod(a,n);
for l=2:length(expon)
expon(l)=mod(expon(l - 1) ∧ 2,n);
end
for i=1:length(array)
x=mod(x*expon(array(i)+1),n);
end
x=mod(x,n);
(i) For a = 6, k = 13 and n = 17, determine with ful
l workings the expon vector and the value of x.
(ii) Mark a well-documented code to implement the RSA algorithm with public keys (e, n) to encrypt and decrypt the plaintext m using the fastexp m-file.
Your cryptogram should take the inputs:
• the public exponent e and modulus n,
• the plaintext m and give the outputs
• factorization of n,
• the euler phi function, φ(n)
• the private exponent d,
• the ciphertext c.
(b) Illustrate three possible attacks on RSA algorithm and explain how the RSA can respond to each of the attacks.
(c) Give details how RSA can be used for digital signatures.
Question 7
(a) Take into account a Diffie-Hellman scheme with a common prime q = 11 and a primitive root α= 2.
(i) Show that 2 is a primitive root of 11.
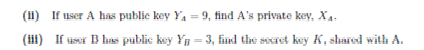
(b) Demonstrate that the Diffie-Hellman key establishment protocol is vulnerable to a "man in the middle attack".
(c) Take into account an ElGamal scheme with a common prime q = 71 and a primitive root α = 7
(i) If B has public key YB = 3 and A chose the random integer k = 2, find the cipher text of the message M = 30.
(ii) If A at the present chooses a different value of k, so that the encoding of M = 30 is C = (59, C2), find the integer C2.
|
Digital forensic investigation
: computer security incident, Trojan Defence, anti-forensics technique, chain of custody, FAT file system, SQLOracleHacks.txt, SQLOracleAttacks.txt, SQLInjection.html
|
|
Computer security incident
: Locard's Exchange Principle, electronic crime scene, modules or DLLs a process, router forensics, Configuration and user, Local logs process and memory, Network Information, File system, Portray the NTP vulnerability of some Cisco IOS routers
|
|
Security vulnerabilities of vc
: single access point (AP), wireless network, CSMA/CA, goals of information security, Wireless LANs, wireless hacking process, Wired Equivalent Privacy (WEP), Open System Authentication and Shared Key Authentication, Initialisation Vector (IV), RADIU..
|
|
Owasp top 10 web application security risks
: Reflected XSS and Stored XSS attack, threat Modeling methodologies, Extended Stack Pointer (ESP) and the Extended Base Pointer (EBP), Canary-based defense to buffer overflow attacks in C language, admin.aspx, Index hijacking, cross-site request fo..
|
|
Cryptosystem
: Block cipher, Primitive root, Confusion, Diffusion, Digital signature, Conventional Symmetric-Key Encryption
|
|
Cyber weapon
: Single Sign On (SSO), Single Sign On (SSO), netstat -an, arp -a, ipconfig /displaydns, MS Config. Means, MS Config. Means, network reconnaissance
|
|
Dos and ddos attack
: Denial of Service attack (DoS) and Distributed Denial of service (DDoS) attack, two-factor authentication system, password ageing, biometric devic, cryptographic attack made Double DES (2DES), Demilitarized Zone (DMZ), SSL protocols
|
|
What is the standard error
: If you have five critical errors, two main faults, and five minor errors, what is the standard error
|