Reference no: EM131221473
A certain user has rated the three computers of Exercise 9.2.1 as follows: A: 4 stars, B: 2 stars, C: 5 stars.
(a) Normalize the ratings for this user.
(b) Compute a user profile for the user, with components for processor speed, disk size, and main memory size, based on the data of Exercise 9.2.1.
Exercise 9.2.1
Three computers, A, B, and C, have the numerical features listed below:
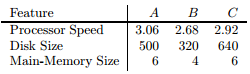
We may imagine these values as defining a vector for each computer; for instance, A's vector is [3.06, 500, 6]. We can compute the cosine distance between any two of the vectors, but if we do not scale the components, then the disk size will dominate and make differences in the other components essentially invisible. Let us use 1 as the scale factor for processor speed, α for the disk size, and β for the main memory size.
(a) In terms of α and β, compute the cosines of the angles between the vectors for each pair of the three computers.
(b) What are the angles between the vectors if α = β = 1?
(c) What are the angles between the vectors if α = 0.01 and β = 0.5?
(d) One fair way of selecting scale factors is to make each inversely proportional to the average value in its component. What would be the values of α and β, and what would be the angles between the vectors?
|
What value minimizes the rmse for the matrix m
: If we wish to start out, as in Fig. 9.10, with all U and V entries set to the same value, what value minimizes the RMSE for the matrix M of our running example?
|
|
Disaster recovery plans in case of earthquakes
: "Disaster recovery plans in case of earthquakes, fires, hurricanes, asteroids that collide with satellites, or other natural or man-made disasters." Many companies have a "risk action plan" to handle unexpected events including network security ev..
|
|
Understanding of multimedia fundamentals
: Demonstrate a working knowledge of basic 2D computer arts creation and modification tools, techniques and strategies - Demonstrate a working knowledge of basic 3D modeling skills, photorealistic enhancement.
|
|
Describe the financial markets in terms of types
: Describe the financial markets in terms of types (primary vs. secondary with IPO and seasoned), Timing (money and capital), Brick and mortar. Be able to list and describe money market instruments such as commercial paper and bankers' acceptances as w..
|
|
Compute the cosines of the angles between the vectors
: In terms of α and β, compute the cosines of the angles between the vectors for each pair of the three computers.
|
|
Straight line method of amortization of any bond premium
: On April 1, 2016 Alpha Company sells $1,000,000 face value of 10% five year bonds which call for semiannual interest payments. The bonds are dated April 1, 2016 so these bonds are issued on an interest date. The market rate at the date of issue is 8%..
|
|
Discuss the technology impact on social
: Discuss the technology's impact on social, ethical, and legal issues. How do you think the role of this technology has changed HCI since its inception? How do you see the future of this technology further changing HCI?
|
|
Customer for accounting services
: On February 1, 2016, the company loaned $100,000 to a supplier and received a 5-year, 12% note. The first annual interest payment is due January 31, 2017. On November 15, 2016, the company received $50,000 from a customer for accounting services to b..
|
|
Power-energy quantification
: A server farm has most of its servers operating at only 50% capacity. The problem is that the power draw from these servers does not scale linearly with the reduced load; that is, when the servers are operating at 50% capacity
|