Reference no: EM13819311 , Length:
The key concepts and frameworks
1. Analyse information security vulnerabilities and threats and determine appropriate controls that can be applied to mitigate the potential risks
2. demonstrate an ability to communicate effectively both written and orally about the management of information security in organisations
Task 1 Specifications - Login to SAP System using your student SAP userid and password and Complete System/User Profile/Own Data fields as specified below
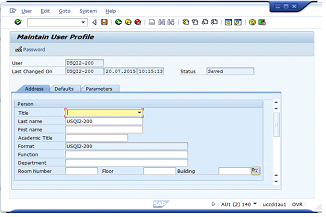
Complete and save the following fields
Title, Last name, First name, Function, Department, Room Number, Floor and Building and provide a screen capture of completed fields in System/User Profile/Own Data
Task 2 Specifications - Analyze SAP Security Audit Log Data.
Userdata.xls is a summarized record of user activity on a client's SAP system. Each record contains the following fields:
USERID
YYYYMM
TCODE
TEXT
TCODESTAT
TCD
TSTATUS
TCOUNT
TTEXT
YYYYMM describes when the user action took place. YYYYMM is useful for summarising user activity by month. TCODE refers to the transaction (option on the menu) performed by the user. TEXT describes the outcome of the action, including its success or failure. Some tcodes are blank. Accordingly, TCODESTAT is an invented transaction code for each action indicating whether the action was successful (-0) or failed (-1). TCD is the same as TCODESTAT, except there is no -0 or -1. TSTATUS indicates whether the action was successful or not (0/1). TCOUNT is the number of times the user has performed this action, with this outcome, in the month YYYYMM. TTEXT is the narrative description of the TCODE.
Task 2 Requirements
You can use software of your choice (spreadsheet, database, statistical package etc) to analyze the provided SAP security audit log data (Userdata.xls), generate appropriate reports and provide an analysis of your findings (hint this assignment 2 task 2 can be done using excel pivot tables or Microsoft Access database SQL queries). Of particular interest are the following reports:
1. Alphabetic list of all actions and their frequency by any selected user, e.g. USER-040.
2. List of users performing unsuccessful activities.
3. List of transaction codes performed, with their frequency by each user.
4. List of users engaging in security-related actions.
5. Top 10 users in terms of frequency of activity.
6. List of users who are dormant - in the range USER-001 to USER-050.
7. You should also produce at least 3 reports/charts/plots based on any of the above previous reports that summarise activity over time using YYYYMM date format.
TASK 3 Specifications - Analyze SAP System-Wide Security Settings.
You are required to review the system-wide security settings on our SAP system. The data file RSPARAM contains an extract from the client's system (Note you should open this file using excel spreadsheet to view the system-wide security settings with the fields aligned correctly. Hint you can use the search function to locate the appropriate SAP system wide security settings and their related values in the data file RSPARAM.txt.
You required to produce a report for Task 3 of Assignment 3 summarizing the current user settings, default settings and recommended settings based on the RSPARAM.txt file.
Your report will consist of a written evaluation of the current settings highlighting any weaknesses, with explanations, and recommendations (1000 words approx.). Note some relevant resources on SAP security will be provided for Tutorials and Assignment 2 discussion forum. The report should take the following form:
ACME DISTRIBUTION COMPANY
SAP System-Wide Security Settings
|
System Setting Value
|
User
|
Default Value
|
Recommended
Value
|
Actual Value
|
|
No auto user SAP*
|
|
|
|
|
|
Failed logins to end
|
|
|
|
|
|
Failed logins to lock
|
|
|
|
|
|
Auto failed unlock
|
|
|
|
|
|
Min password length
|
|
|
|
|
|
Password expiry (days)
|
|
|
|
|
|
Idle logout (seconds)
|
|
|
|
|
|
No check on Tcodes
|
|
|
|
|
|
Default login client
|
|
|
|
|