The steps that occur when we request a ASPX page are as follows:-
1) The browser sends the request to the webserver. Now assume that the webserver at the other end is IIS.
2) Once the IIS receives the request he looks on which engine the request is served. Whenever I mean engine that means the DLL who can parse this page or compile and send a response back to the browser. Which request is to map is decided by the file extension of the page requested.
Depending on the file extension some mapping are as follows:
1) .aspx, for the ASP.NET Web pages,
2).asmx, for the ASP.NET Web services,
3).config, for the ASP.NET configuration files,
4).ashx, for the custom ASP.NET HTTP handlers
5).rem, for remoting the resources
6)Etc
You also can configure the extension mapping to which engine can route by using the IIS engine.
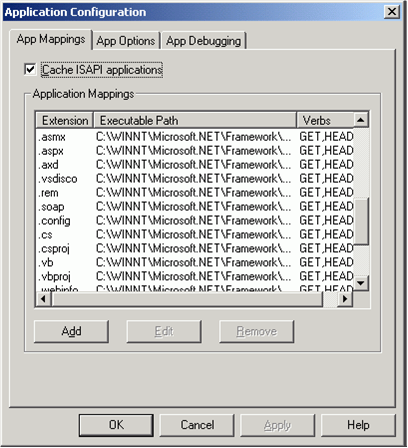
For example an ASP page will be sent to the old classic ASP.DLL to compile. While the .ASPX pages will be routed to the ASP.NET engine for compilation.
7) We will see how an ASP.NET page that is ASPX pages generation sequence occurs. Once IIS passes the Request to the ASP.NET engine page has to go through two section HTTP module section and HTTP handler section. Both of this section has their own work to be completed in order that the page is properly compiled and sent to the IIS. The HTTP modules inspect the incoming request and depending on that they can change their internal workflow of the request. The HTTP handler actually compiles the page and generates the output. If you see your machine.config file you will see the following section of HTTP modules.
d name="OutputCache" type="System.Web.Caching.OutputCacheModule" />
d name="Session" type="System.Web.SessionState.SessionStateModule" />
d name="WindowsAuthentication" type="System.Web.Security.WindowsAuthenticationModule" />
d name="PassportAuthentication" type="System.Web.Security.PassportAuthenticationModule" />
d name="UrlAuthorization" type="System.Web.Security.UrlAuthorizationModule" />
d name="FileAuthorization" type="System.Web.Security.FileAuthorizationModule" />
d name="ErrorHandlerModule" type="System.Web.Mobile.ErrorHandlerModule, System.Web.Mobile, Version=1.0.5000.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" /
>
The mapping above will show which functionality is to be handled by which Namespace. For e.g. FormsAthuentication is handled by "System.Web. Security.FormsAuthenticationModule". If you see at the web.config section HTTP module is where the authentication and authorization happens.
d verb="*" path="*.vjsproj" type="System.Web.HttpForbiddenHandler" />
d verb="*" path="*.java" type="System.Web.HttpForbiddenHandler" />
d verb="*" path="*.jsl" type="System.Web.HttpForbiddenHandler" />
d verb="*" path="trace.axd" type="System.Web.Handlers.TraceHandler" />
d verb="*" path="*.aspx" type="System.Web.UI.PageHandlerFactory" />
d verb="*" path="*.ashx" type="System.Web.UI.SimpleHandlerFactory" />
...
Depending on the File extension handler it decides which Namespace will generate the output. e.g. All .ASPX extension files will be compiled by the System.Web.UI.PageHandlerFactory
Once the file is done it will be send back again to the HTTP modules and from there to IIS and then to the browser.
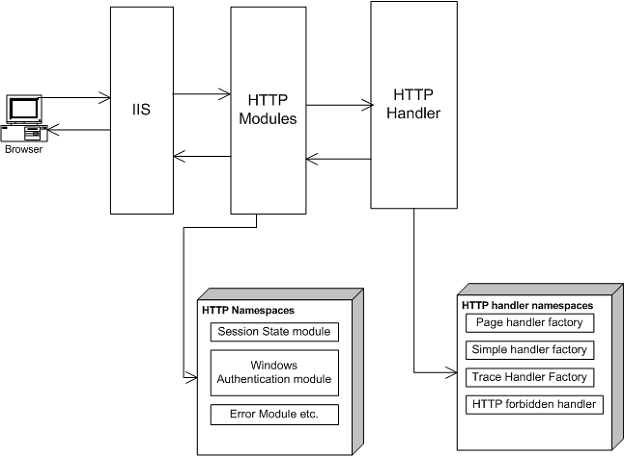
Figure:-IIS flow from various sections.