Q. Microcomputer - Controlled Breadmaking Machine?
Figure shows a simplified schematic diagram of a microcomputer-controlled breadmaking machine. A microcomputer along with its timing circuit, keypad, and display unit controls the heating resistor, fan motor, and bread-ingredient mixing motor by means of digitally activated switches. An analog temperature sensor, through an A/D converter, provides the status of temperature to themicrocomputer.Adigital timer circuit counts down, showing the time remaining in the process.
The control programs are stored in ROM and determine when and how long the machine should mix the ingredients added to the bread pan, when and how long the heating resistor should be turned on or off for various parts of the cycle, and when and how long the fan should be on to cool the loaf after baking is finished. The parameters such as light, medium, or dark bread crust are entered through the keypad into RAM.
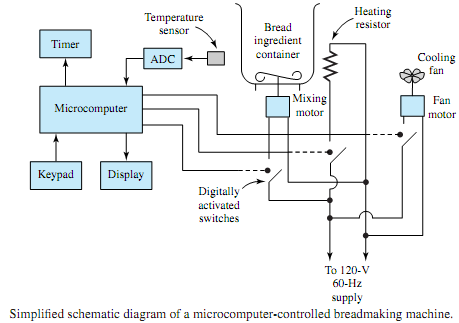
According to the programs stored and the parameters entered, the machine initially mixes the ingredients for several minutes. The heating resistor is turned on to warm the yeast, causing the dough to rise while a temperature of about 90°F is maintained. The time remaining and the temperature are continually checked until the baked loaf is cooled, and the finished bread is finally ready in about 4 hours.
Microprocessors and computers in various forms are used extensively in household appliances, automobiles, and industrial equipment.