DNS Message
There are the only two kinds of DNS message DNS query and reply messages. Further mote both query and reply message have the same format as shown in figure. The semantics of the various fields in a DNS message are as follows.
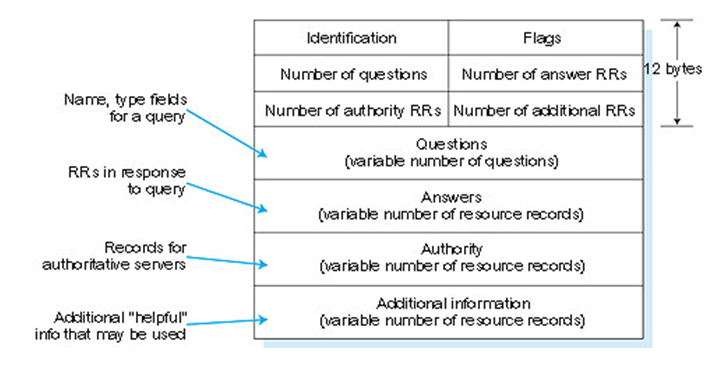
Figure DNS message format
The first 12 bytes is the header section which has a number of fields. The first field is a 16 bit numbers that identifies the query. This identifier is copied into the reply message to a query allowing the client to match received replies with sent queries. There are a number of flags in the flag field. A 1 bit query reply flag indicates whether the message is a query or a reply a 1 bit authoritative flag is set in a reply message when a DNS server is an authoritative server for a queried name. A 1 bit recursion desired flag is set when a client host or DNS server desired that the DNs server perform recursion when it doesn't have the records. A 1 bit recursion available field is set in a reply if the DNS server supports recursion. In the header there are also four number of fields. These fields indicate the number of occurrences of the four type of the data section that follow the header.
a.The question section carries one or more question that is queries for information being sent to a DNS name server. This section includes a name field that containing the name that is being queried and a type field that indicates the type of question being asked about the name for example a host address associated with a name or the mail server for a name .
b.Answer carries one or more resources records that answer the questions indicated in the question section above.
c.Recall that in each resource records there is the type ( for example A , NS, MNAME, and MX), the value and the TTL. A reply can return multiple RRS in the answer since a hostname can have multiple IP address.
d.The authority contains one more resource records that paid to authoritative name servers that can be used to continue the resolution process.
e.The additional section conveys one or more resource records that contain additional information related to the query that is not strictly necessary to answer the queries.