Overview of Data transmission network model
A network is a combination of hardware and software that sends data from one location to another. The hardware consists of the physical equipment that carries signals from one point of the network to another. The software consists of instruction sets that make possible the services that we expect from a network.
When sending data from software to actual physical transmission link (medium), there are several layers. Each layer provides certain services. The Open System Interconnection (OSI) layer model is the international standard, and it has 7 layers.
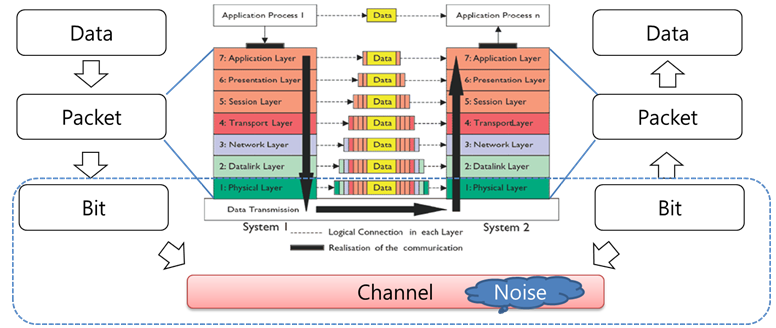
Fig. General digital control system
When the digital data is transmitted through real line, these digital data should be converted to either a digital signal or an analog signal. In this project, we will convert a data to a digital signal. There are several conversion methods, and we use one of the simple methods as below.
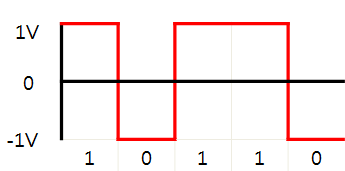
Fig. Example of signal conversion from digital data
The waveform pattern of 1V or -1V used to represent the 1s and 0s of a digital data on a transmission channel. Suppose the transmission link is not ideal, some noises can be added to original signal. If the amplitude of the noise follows the normal distribution, the noise is called Gaussian noise.
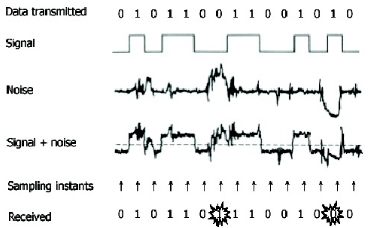
Fig. 3. Data transmission on noise channel
The function that generates 'Gaussian noise' will be given, and the argument of the function is SNR (Signal-to-noise ratio) dB(decibel). SNR is defined as the ratio of signal power to the noise power, and SNRdB is defined as 10*Log(SNR). Large SNR means that signal power is relatively higher than noise power, so noise is less effective. If noise is less effective, received data has less error.
Even though sending the data on the channel whose SNR is identical, reliable communication is possible when using error-detecting code or error-correcting code.