Reference no: EM131402992
Information System Security Assignment
Differentiate Following:
1. Threat and Attack
2. Active Attack and Passive Attack
3. Interruption and Interception
4. Virus and Worm
5. Sniffing and Spoofing
6. Phishing and Pharming
7. Substitution and Transposition
8. Symmetric Key and Asymmetrical Key
9. Vigenere Cipher and Vernam Cipher
10. Cryptography and Steganography
EXERCISE:
Note: - Map A-Z with 0-25
1. Do the Encryption using a Caesar Cipher where key K=3. Plain Text: U V PATEL COLLEGE OF ENGINEERING
2. Do the Encryption using a Vigenere Cipher where Key is dollars. Plain Text: the house is being sold tonight Also Do the Decryption process.
3. Do the encryption and decryption using Playfair cipher Plain text: the key is hidden under the door pad Key: guidance
4. Do the Decryption using a Play fair Cipher where Key is COMMING.
Cipher Text: HEXMRXAWLDUMGBSUCAIA
5. Do the Encryption using a Play fair Cipher where Key is CONGRUENCE 179. Plain Text: NUMBER THEORY Also Do the Decryption process.
6. Do the encryption and decryption using Hill Cipher on plain text "CODE"
7. Do the Encryption us ng a Hill Cipher on plain text "GOOD"
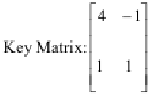
Also Do the Decryption process.
|
Discuss hospitality marketing in general
: Discuss hospitality marketing in general. Draw illustrations from one successful company?
|
|
What linguistic or religious factors are involved
: What linguistic or religious factors are involved? Are certain words in the lyrics from a non-English language? Is there evidence of a dialect? What cultural or ethnic groups are represented in this song?
|
|
Can big replicate its system in other industries
: How proprietary or defensible is BIG's system? Could one of the major toy companiesreplicate it? Why or why not? Can BIG replicate its system in other industries, such as lawn and garden?
|
|
What are two ways in which national wealth is accumulated
: Give two reasons that the unemployment rate may not measure correctly what we want it to measure.
|
|
Do the encryption and decryption using playfair cipher
: 2IT603: Information System Security Assignment. Do the Encryption using a Vigenere Cipher where Key is dollars. Plain Text: the house is being sold tonight Also Do the Decryption process. 3. Do the encryption and decryption using Playfair cipher Pla..
|
|
Investigate the link between given two variables
: Investigate the link between these two variables by conducting a complete simple linear regression analysis of the data. Summarize your findings in a professional report.
|
|
Determining the wider organisational context
: You work for a health food manufacturer. It has come to your attention that other organisations in the industry have introduced products that they are promoting as being highly healthy and nutritious; however, the new products are very high in sug..
|
|
Evaluating and refining idea
: What testing and exploration techniques might be utilised in order to determine whether your idea can be applied? Draw up a plan or schedule for the purpose of examining, testing, evaluating and refining your idea. (1-2 pages)
|
|
Describe spatial distribution of population in monsoon asia
: Write a couple of sentences to describe the spatial distribution of the population in Monsoon Asia (using the population dot map above). Suggest reasons for the spatial distribution of population that you see in Monsoon Asia.
|