Reference no: EM131015262
1. Let's consider the Kerberos authentication scenario shown in Figure 1. Before the client user can prove his identity to the Server in Step 5, the client needs to first get a (service) ticket from the Ticket Granting Server (TGS) through Step 3 and Step 4. Moreover, in order to get a ticket from TGS, the client has to firstly go through Step 1 and 2 with the Authentication Server (AS) to get the TGT (ticket granting ticket).
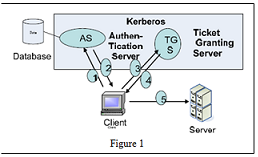
1.1:In Figure 1, only one machine knows the long term key of the TGS besides the TGS, who is it?
1.2: In Figure 1, say True or False to the following statement: "AS knows the long term key of the Server".
1.3: In Step (2), AS will send the TGT to the client. Say True or False to the following statement: "To enable the client to see what is inside the TGT, the TGT will be encrypted by the client user's long term key, which is a transformation of the user's password."
1.4: In Step (3), the client needs to send two things to TGS: the authenticator and the TGT. Since the TGT contains the user's identity information, it seems that the authenticator is useless. However, without the authenticator, John (the attacker) may launch a serious attack. What can this attack do?
1.5: With the authenticator, the attack mentioned in Question 1.4 will be defeated. Why?
1.6: To prevent attacks, the authenticator must be encrypted in Step (3). However, the client does NOT know the long term key of the TGS. How can Kerberos let the TGS know the authenticator encryption key? Please give a complete answer
1.7: After TGS verifies the client's identity, TGS will issue a ticket to the client. What information items are included in this ticket?
1.8: After a while, the client will receive the ticket. Then (in Step 5), the client will send the ticket to the server. However, this ticket itself is
NOT sufficient for the server to offer the service to the client because Mallory may launch a serious attack. What can this attack do to fool the server?
1.9: Because of the problem mentioned in Question 1.8, the client also needs to send another authenticator to the server. The authenticator will be encrypted by which key?
1.10: When the Server receives the authenticator and the ticket from the client. The server will compare the information items contained in the authenticator and the ticket to authenticate the client user's identity. Please give a detailed answer on how such comparison will be done?
2. To avoid letting every server know every user's password, Kerberos wants to enforce the ticket-based service access idea. However, this idea is facing three security threats. What are they?
|
Types of natural and man-made disasters and attacks
: What type of natural hazard do you think is the most significant or troublesome to emergency managers - what type of man-made hazard do you think is the most significant or troublesome to emergency managers? Why?
|
|
Was the study design cross-sectional or longitudinal
: What were the units of analysis? Were they appropriate for the research question? Was the study design cross-sectional or longitudinal? Was a sample or the entire population of elements used in the study? What type of sample was selected
|
|
Activity rate for product design activity cost pool
: What is the activity rate for the Product Design activity cost pool? Product design activity cost pool $ per product
|
|
Predominantly substantive approach
: Which of the following audit strategies would be most appropriate when an auditor has assessed a predominantly substantive approach is necessary to determine inventory quantity?
|
|
What information items are included in this ticket
: When the Server receives the authenticator and the ticket from the client. The server will compare the information items contained in the authenticator and the ticket to authenticate the client user's identity. Please give a detailed answer on how..
|
|
Research the greek crisis and draw your own conclusions
: Your assignment is to research the Greek crisis and draw your own conclusions on what the outcome will be for survival. Will they exit the Euro? Or rebuild their economy?
|
|
Predetermined overhead rates
: Machining Assembly Direct labor hours 16,000 12,000 Direct labor cost $ 20,000 $ 15,000 Machine-hours 5,000 1,000 Manufacturing overhead $ 25,000 $ 30,000 What predetermined overhead rates would be used in the Machining and Assembly Departments, r..
|
|
Estimated monthly contribution margin per cable
: 1. What is the estimated monthly contribution margin per cable subscriber for CableVision in 2016? 2. What are the estimated total monthly fixed costs for CableVision in 2016?
|
|
Paper - interracial marriage in rural america today
: Write a paper on given topic. Topic - Interracial Marriage in Rural America Today.
|