Reference no: EM131227064
Introduction
This case study has been divided into six components.
You are to design a network, research and source appropriate devices justifying choices (feasibility, efficiency, etc), subnet the network using VLSM, and assign IP addresses to the appropriate devices. You will also be required to implement security by applying access control lists to filter traffic and provide a plan for performance management.
Scenario
A large accounting company has asked you to assess and redesign their corporate network. They are also opening two new branches in Australia (Brisbane and Sydney), which will require new equipment. They wish to maintain Frame Relay for all WAN links.
PART 1 - Network specifications and topology diagram
PART 2 - Subnet the network using VLSM, and assign IP addresses to the appropriate devices.
PART 3 - Research and source appropriate devices justifying choices (feasibility, efficiency, etc) with a Weighted Scoring Model (WSM) and documented report.
PART 4- Security by applying Access Control Lists (ACLs) to filter traffic
PART 1 - Network specifications and topology diagram Network Specifications
You have been given the rough sketch for the network topology below. You are to draw the network using Visio, subnet the network (see case study part 2), and assign port numbers and IP addresses to ports.
You must save your Visio diagram as a .gif and import to your Excel spreadsheet (use one worksheet for the diagram (i.e., nothing else on that worksheet).
Network Structure
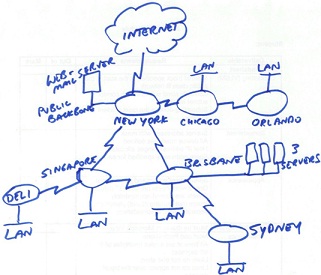
Hardware
- Only include one switch in you diagram for each LAN (even if more are required)
- The Internet router port address is 200.37.21.1/30
- There is no user LAN on the New York router, only the Internet connection and the public backbone containing a Web and mail server.
PART 2 - Subnet the network using VLSM, and assign IP addresses to the appropriate devices.
Each location has the following number of hosts
|
Chicago
|
1000
|
|
Orlando
|
500
|
|
Brisbane
|
250
|
|
Sydney
|
48
|
|
Singapore
|
300
|
|
Deli
|
150
|
Subnetting
Use VLSM to subnet the network topology using a public class B network. You are to use the table format below to provide the subnet details.
Table 1. Subnets (including WAN subnets)
Spreadsheet Columns: Subnet name, subnet address, subnet mask (in slash format), first useable address, last useable address, broadcast address, static address range and DHCP address range (all addresses to be in dotted decimal notation)
Table 2. Router Interfaces
Spreadsheet Columns: Location, interface, IP address, subnet mask (in slash format)
Table 3. Servers
Spreadsheet Columns: Location, server name, IP address, subnet mask (in slash format)
Additional requirements:
- Choose one public B class network address for the entire network and subnet this block of addresses to optimise spare addresses for future expansion.
- Place the WAN subnets in the blocks directly following the LAN address space.
- Add 100% to each subnet to allow for growth in the number of hosts specified for each LAN. Do not allow for any growth in the number of servers
- DHCP will to be used for IP address allocation for hosts in each subnet and these ranges are to be allocated for each LAN
- Static IP addresses are to be allocated where appropriate
- The ISP has given us an IP address of 200.37.21.1/30 for our Internet connection at New York
PART 3 - Research and source appropriate devices justifying choices (feasibility, efficiency, etc).
You are to research and submit a project procurement plan for the Brisbane and Sydney networks. The devices you must include are all relevant network devices (Layer 2 and 3 only) and user PCs.
Your project plan and final recommendations should be based on a Weighted Decision Matrix (similar to the WDM you did in the Procurement Practical.
Your plan should use the following structure:
Your project plan is to contain the following components:
Executive summary
- Give an overview of the project plan and feasibility outcome.
- This should briefly describe the project's goals and/or purpose, the scope and how it will be achieved within time and budget.
- Should be approximately 500 words.
Introduction and Project organisation.
- Project overview - Purpose and detailed scope analysis
- User and stakeholder analysis
- Budget declaration
Weighted Decision Matrix - hardware resource requirements analysis.
- Justifications for priorities and attributes given in the matrix.
Budget
- Final project costing of hardware only (do not include labour)
PART 4- Security by applying access control lists to filter traffic
Write the ACL configuration commands required to address the following security requirements. You must also provide the configuration commands required to apply the security rules to the appropriate router interface.
Requirements for all ACLs
- Do not include the commands to enter configuration mode
- Provide only the commands required to address the questions
- Do not include router prompts
- ACLs are to be placed in the optimal position to minimise bandwidth unless the location of the ACL is specified
- Each ACL must use the next lowest available ACL number on that router
- You are not to rely on the implicit deny any any.
- If a protocol has multiple port numbers (as per RFC 1700) use only the lowest port number for this exercise
- If a protocol operates on both UDP and TCP then apply a rule for both
- No ACL is required on a port where all traffic is permitted.
- Remember to state the question number and the router to which you are applying the ACL.
a) Access to the Internet and public backbone:
Apply these ACL/s to serial 0/0 on the New York Router
1. External hosts outside the organisation (on the Internet) must only be able to access the web server on the public backbone using HTTP and HTTPS
2. No other external access is permitted into the organisation from the Internet
3. Internal hosts must only be able to communicate out to the Internet using HTTP and HTTPS .
b) The United States LANs
4. The Chicago and Orlando LANs are to have unrestricted access to the web server and other LANs in the United States - except that both LANs are to be restricted from initiating ping requests
5. They are to have no other access outside of the United States, except for New York and Chicago who are to be able to communicate with the database server at Brisbane using TCP port 1433. In addition, the Orlando LAN is to be able to communicate to all three servers at Brisbane using SSH
6. Apply the rules above for the Chicago and Orlando LANs separately on the router associated with each LAN.
c) The Australian LANs
7. The Brisbane and Sydney LANs are to have HTTP and HTTPS internal access only to the web server on the public backbone. They will also require access to DNS which is also running on the web server. Implement these ACLs on the Brisbane router only.
8. The Brisbane LAN is to have unrestricted access to all 3 servers - except for Telnet and FTP which are to be blocked.
d) Asian and Indian LANs
9. Singapore and Deli LANs are to have access to the database server (SQL Server) using TCP port 1433. All other access from the LANs is to be blocked.