Reference no: EM13843360
Lab: Vulnerability Assessment
Probably the most overlooked process in any type of security system is the vulnerability assessment. Vulnerability assessments are incredibly useful (and necessary) tools. They provide a structured method for determining what assets need to be protected, what threats against the assets exist, what security vulnerabilities currently exist, the cost of losing the asset, and mitigating the risk to the asset. In a nutshell, a vulnerability assessment done properly will form the basis of your entire security plan(s) for your organization.
If vulnerability assessmentsare so important, why are they often only partially completed (if they are even completed at all)? The answer is simple, they take time, and require the identification and fixing of current security problems (two things that most people would rather just ignore). For this lab, you will conduct your own vulnerability assessment. Your finished assessment will be a multi-page written document containing the following sections.
Part 1: Asset Identification
Although this course concerns IT security, I find it is much easier to learn the vulnerability assessment process using physical items instead of things like computer network assets. Your first step in this lab is to identify the ten most important personal assets you own. These assets could be anything from your laptop or television, to your car or motorcycle. Also, do not simply pick the ten items you own which are worth the most amount of money. It is very possible that your top ten asset inventory might include items which hold a great deal of sentimental value instead of only monetary value. Think about what you own, and pick the top ten items which mean the most to you. For this section of your assessment document, provide your ten asset inventory listing your most prized possession first, second most prized possession second, and so on.
Part 2: Threat Evaluation
The best way to determine what threats against your assets exist is to create an attack tree. An attack tree is a visual representation of how a given asset might be attacked. In the case of this lab, attacked most likely means stolen or destroyed. On the following page, I have included an attack tree for one of my most prized assets. I only included theft based attacks for this particular attack tree because the destruction route was just a little too morbid!
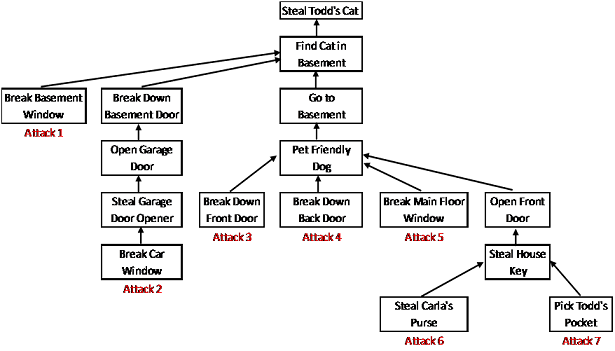
To complete this section of your assessment, pick the number one item from your asset inventory and build your own attack tree. Take your time and try to think of, and document, every possible attack that could result in the theft of your most prized possession. While my example attack tree looks pretty good, I can think of a few more potential attack routes for stealing my cat. If necessary, break your attack tree into multiple pages to cover all potential attacks. Part of your grade for this lab will depend on the thoroughness of your attack tree.
Part 3: Vulnerability Appraisal
Now that you have completed your attack tree, you can move onto identifying your current security vulnerabilities. In order to determine how you can better secure your asset, you need to identify the weaknesses which allow attacks to take place. To begin, number the potential attacks from your attack tree from left to right starting with one. For my example attack tree, the attack beginning with "Break Basement Window" would be attack #1. After you have created a numbered list of all the attacks from your attack tree, determine what current security weakness(s) allows each attack to take place. For example, in my list for attack #1, the security weakness might be a large ground-level basement window with no bars or other security feature. For attack number two, I can think of at least two vulnerabilities; parking my truck on the street at night, and keeping a garage door opener in my truck. For this section of your assessment, list the security vulnerabilities for each of your numbered attacks. Part of your grade will depend on your identification of the possible vulnerabilities relating to the attacks shown in your attack tree.
Part 4: Risk Assessment
At this point you probably have a pretty long list of attacks, and associated vulnerabilities which allow those attacks to be carried out. The next step is to categorize the different security vulnerabilities (risks) you identified in Step 3. Some of these attacks and corresponding vulnerabilities will have the potential to be much more harmful than others. This section is where you rank the possible attacks and vulnerabilities.
Risk factors (or what makes some attacks/vulnerabilities worse than others) depend on several factors. How likely is the attack to succeed (the more likely, the worse the risk)? How damaging is the actual attack (the more damage caused, the worse the risk)? How damaging will it be if the asset is actually stolen (the more expensive or irreplaceable the asset, the worse the risk)? The highest risk attack/vulnerability combination are those which include an attack which is easy to execute, causes a lot of damage, and succeeds in stealing or destroying an asset which is extremely valuable.
Looking at my example attack tree, I would rank the first attack as high risk. It is easy to break the basement window, and the result is not only the theft of an irreplaceable asset (my cat), but a house which is now unsecure until the attack is noticed. I would rate the last attack in the tree low risk. While obtaining a key to my house is very damaging, and my cat would still be stolen, the chance of someone picking my pocket and stealing my keys without me noticing is low. It's not that I think it would be impossible for a professional pick-pocket to steal my keys, but rather that I really doubt anyone is going to hire a professional pick-pocket just so they can steal my cat. In addition, my key chain includes not only my house key, but my office and car keys...I'll notice they are gone quickly even if they are stolen. For this section of the assessment, work through your numbered list from Part 3 and designate each attack/vulnerability combination as high, medium, and low risk. Include a descriptive sentence for each item in your list describing why you assigned the high, medium, or low risk rating.
Part 5: Risk Mitigation
The final step in a vulnerability assessment is to decide what to do about any of the major security risks you have developed through the proceeding steps. While the ultimate goal would be to attempt to address all risks you identified in Step 4, due to difficulty or expense, this is rarely accomplished (or even attempted). Most organizations will certainly attempt to address the high risk items on the list from Step 4. If enough organizational resources (money, time, expertise, etc.) is left after addressing the high level risks, then medium level risks are addressed. Often times low level risks might not be addressed at all, or might be partially addressed (putting a fake alarm system sticker on a window for example).
Keep in mind that there may be several ways to address the vulnerabilities. For example, there are a few different ways to address attack 3 in my example attack tree. I could buy a metal front door (much more secure than the wood door I have now). I could install an alarm system (this might address many potential attacks in the tree, but would be expensive). I could train my friendly dog to be an attack dog. I could install a locking door between main level of the house and the basement. I could buy a comfortable cage for my cat, bolt the cage to the floor, and lock the cat in the cage whenever I leave the house (effective, but not very nice for the cat, and I'd probably forget to put the cat in the cage anyway).
To complete this section of your vulnerability assessment, list your high risk level items from Step 4, and describe how they could be addressed as demonstrated above. If you have fewer than three high risk items, explain how you would address your medium risk items.
Finally, provide a short summary which describes the best possible way in which you think your asset should be secured. This summary should address why you decided on this particular course of action, and should consider things like cost or time necessary to implement your decision. Keep in mind that the best possible plan might be too costly, or just not realistic in terms of time commitment (I'm not going to hire a body guard for my cat, or take the time to physically secure my cat in a panic room every time I leave the house no matter how secure that makes my cat).
When your vulnerability assessment is complete (I would also like it to be professionally formatted), submit it on the Lab 2 assignment page.As mentioned during several steps above, your grade will depend heavily on the completeness and comprehensiveness of your assessment.