Reference no: EM13835685
Question 1:
Snort Rules
Scenario
A small company has a network set up behind a NAT router. The router is connected to the Internet via a single ISP provided dynamic IP address. The ISP provided access address may change over short periods of time.
The internal network is RFC 1918 Category 2 compliant, and uses the private address space 192.168.2.0/24. The gateway router is configured to use DHCP allocated IP addresses to internal hosts as they connect. However, a record is kept within the router of what IP addresses have previously been allocated to specific MAC addresses. Whenever those MAC addressed hosts disconnect from and later reconnect to the network they are reallocated the same IP address. It is only if the router has a power off episode, or is manually reset, that allocation of different IP addresses may occur (and even then, the same addresses may be allocated as before).
The company operates an approved internal web server at 192.168.2.21:80, to facilitate in-house development of web pages and web sites that will later be deployed to an external server for public access. It is a company policy that only one approved internal web server is to be in operation on the network.
You are the company IT Manager.
It has come to your notice that a company employee has set up a rogue web server on the internal network, using a personal laptop. The employee is using that web site to provide undesirable material to a small clique of employees, to whom the web server address has been provided secretly.
The company CEO has requested you to:
1. Obtain hard evidence that an employee is in fact using a personal laptop to set up a rogue web server.
2. Find out what other employees are accessing the rogue web site.
Considerations
• The rogue web server may be on any internal IP address, and will be using any of the ephemeral ports. It will not be using a well-known port.
• The clients accessing the rogue web server may come from any internal IP address using any ephemeral port.
• The MAC addresses of all company host devices are on record.
• The MAC address of the device being used to host the rogue web server, and the MAC addresses of all devices that connect to the rogue server, need to be obtained for later use as evidence.
Technical Approach to the Solution
To carry out the CEO's request you have decided to:
A) Use Wireshark to capture packet data on the internal network.
B) Use snort to monitor for any internal network HTTP traffic destined for any internal host on any port address other than the authorised company internal web server and produce an alert message.
The snort monitoring will identify when breaches have occurred. The Wireshark pcap file containing the captured packets can be time correlated with the logged snort alerts to obtain MAC addresses for source and target.
Your Task
You are to write a .conf file containing the snort rule(s) that will accomplish the technical approach to a solution.
1.1. Identification of Addresses By inspecting the sample alert.ids entries given above you should be able to identify:
1. The IP address, and port number of the device hosting the rogue web server.
2. The IP addresses of all devices that access the rogue web server.
You are to enter this information into a table (see following), and submit it with your assignment submission document.
Explain in your own words how the MAC addresses of these devices can be discovered from the pcap file.
Question 2:
Wireless Protocols
A. Describe 802.1x authentication and the steps that when a wireless client connects to a network using RADIUS server for authentication.
B. Explain the PEAP protocol - how does it differ from EAP and what EAP deficiency does it address?
C. What makes a brute-force attack both particularly difficult and potentially easy on a wireless network using AES/CCMP encryption and 802.1x authentication? Hint: What do you need to know in order to attempt the attack?
D. Assume an office wireless network was only configured with AES/CCMP encryption (i.e. no additional authentication standards). What problems would this cause?
E. Assume an office wireless network was only configured with 802.1x authentication (i.e. no additional encryption). What problems would this cause?
Question 3:
The Deep Web (Bergman, 2000), also known as the Dark Web, is a parallel Internet found only through encrypted private networks beyond the reach of search engines.
Your task is to write a two-page summary (around 500 words including references) addressing the following points:
1. Describe the technical characteristics of the Dark Web ensuring you explain how it works and its underlying technologies
2. Discuss the impact of the Dark Web on society. In addressing this point, ensure you discuss its purpose and the forces behind it
3. The future of the Dark Web. How problematic will it be in years to come? What role will information security practitioners play to tackle this issue?
Question 4:
Kerberos Authentication Protocol
Kerberos is one of the most secure authentication protocols being used today. The Kerberos authentication protocol is very briefly described on page 280 in Chapter 8 of the Ciampa textbook. You are required to do personal research to complete the following questions regarding this topic:
A. Give your general description of the Kerberos authentication protocol.
B. Explain the term: Authenticator used in the Kerberos authentication protocol.
C. In the Kerberos authentication protocol, there are 3 basic roles: client, server and Key Distribution Centre (KDC). Give your description of each of them.
D. By explaining the term: Session Ticket, describe how a session key is created by KDC, and distributed to the client and the server
E. Describe the mutual authentication procedure between the client and the server after the client obtains the session ticket
Question 5:
You are the Chief Information security Officer (CISO) of a small medium sized - accounting Services Company. In the last few weeks, senior staff have been complaining that some confidential information has been disclosed via email without any authorisation. You are approached by the Chief Information Officer (CIO) to discuss the issue and see the most appropriate way to tackle this problem. You suspect that some of the employees might be using their technical skills to access sensitive information either from the mail servers or during transmission. To counteract this malpractice, you suggest the CIO the implementation of encryption. Before you actually implement the system, you want to conduct a pilot using the GNU Privacy Guard (GPG) software.
The pilot requires that you install GNU Privacy Guard (GPG) software onto your own computer and complete the following activities.
Note: The GNU Privacy Guard is available for free download from https://www.gnupg.org/ and "A Practical Introduction to GNU Privacy Guard in Windows" by Brendan Kidwell is available at https://www.glump.net/howto/gpg_intro
After installing GPG software onto your own computer, complete the following tasks:
1. Generate your own key-pair by using GPG software and do not create a pass-phrase for your private key (in a real world this is not a good practice. Just for the sake of this assignment, do not create a pass-phrase). You need to use screen-shots to show that you have successfully completed this task. A valid screen-shot is similar to the one shown in Figure 1. Pay attention to the red circles, which demonstrate the success of key pair generation.
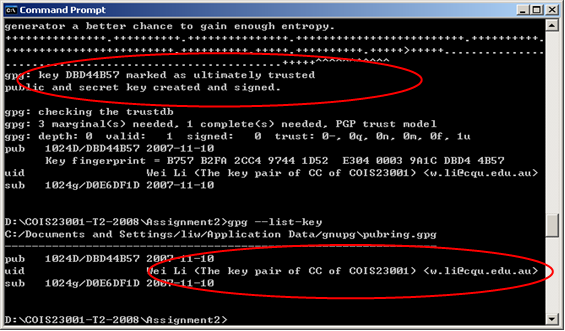
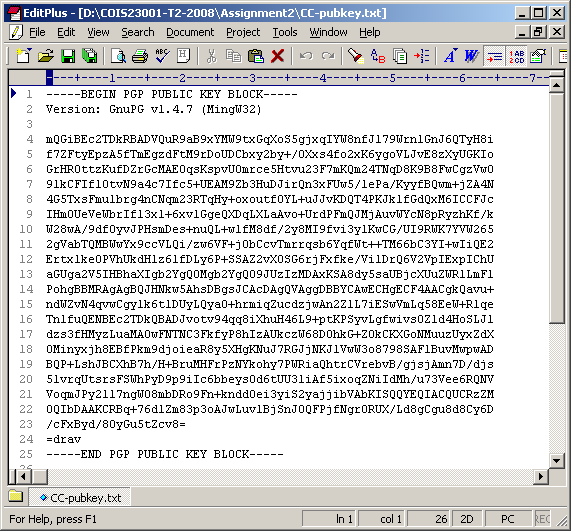
2. Export your public key and paste it into your assignment document. You need to use two screen-shots to show that you have successfully completed this task. One screen-shot is to show the use of gpg command and the other is to show the exported public key. For example, the screen-shot in Figure 2, shows a public key, which is exported into the file: CC-pubkey.txt.
3. Explain the steps how to import your Lecturer's public key from the key-server https://pgp.mit.edu (your lecturer created a public key and stored it at the MIT PGP Public Key Server). Include in the assignment document the gpg command line, individual options you used and their meaning. As above, use screenshots of website interactions, with accompanying explanations of the screenshots to explain the steps how to import your Lecturer's public key from the key-server https://pgp.mit.edu.
4. Create an ASCII text file to store your full-name, your student number, and your student CQU email address (please do not use any other email address). Then using your lecturer's public key, encrypt this text file. The resulting file should also be ASCII armored so that it is readable once decrypted by your lecturer / tutor. Failure to do so will result in loss of marks. Submit the resulting encrypted file along with your assignment solutions document (word document) via the online submission system and following the naming convention given above.