Reference no: EM131428171
This paper consists of SIX (6) questions. Answer any FOUR (4) questions in the answer booklet provided. All questions carry equal marks.
Question 1
(a)

|
|
John - PC
|
Router - A
|
Router - B
|
Alex - PC
|
|
IP address
|
1.1.1.1/24
|
Fa0/0 - 1.1.1.254/24 Fa 0/1 -192.168.1.1/30
|
Fa0/0 -2.1.1.254/24 Fa0/1 -192.168.1.2/30
|
2.1.1.1/24
|
|
Mac Address
|
1111.1111. 1111
|
Fa0/0 - 2222.2222.2222
Fa0/1 - 3333.3333.3333
|
4444.4444.4444
5555.5555.5555
|
aaaa.aaaa.aaaa
|
Figure 1(a)
Provide a step-by-step procedure of the routing process that takes place when user John sends a packet to user Alex.
(b)
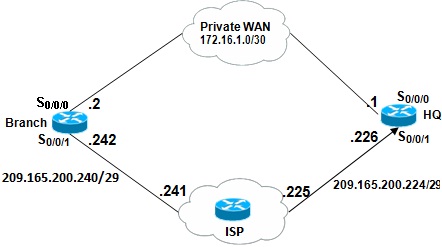
Figure 1(b)
The HQ and the Branch of ABC Corporation are connected through a private WAN (cloud) as well as via the Internet for redundancy purposes as sown in Figure 1(b).
i. Identify the type of routing used between the routers and the Branch that facilitates the high availability and also prevents layer-3 looping.
ii. Explain the working principle of your proposed solution.
iii. Explain the disadvantage of your proposed solution.
Question 2
(a)
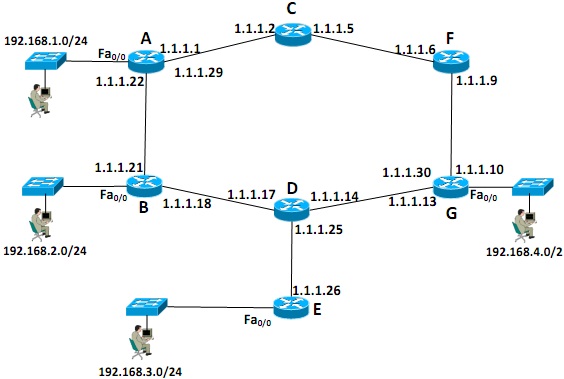
Figure 2(a)
Using Bellman Ford algorithm, construct a topology database of the network for router - A as shown in Figure 2(a) and highlight the entries that are selected for routing table.
(b) Even though Enhanced Interior Gateway Routing Protocol (EIGRP) is classified as a Distance Vector (DV) Protocols, its working principles is different from conventional DV protocol. Discuss any FIVE (5) behaviors of EIGRP which clearly illustrate these differences.
(c) As a network administrator, explain in which situations you would choose to use the distance vector routing protocols.
Question 3
(a)
Router#sh ip route
********Output removed *******
Gateway of last resort is not set
R 192.168.1.0/24 [120/1] via 192.168.2.1, 00:00:15, FastEthernet0/0
********Output removed *******
Figure 3(a)
Analyze the output shown in Figure 3(a) (shown in bold) of the command "show ip route" and explain its components and each's significance.
(b)
Router# show ip eigrp topology
IP-EIGRP Topology Table for AS 1
Codes: P - Passive, A - Active, U - Update, Q - Query, R - Reply, r - Reply status
<output omitted>
P 10.10.12.0/24, 1 successors, FD is 5514496
via 172.16.1.38 (5514496/28160), Serial0/1/0 via 172.16.1.42 (7693056/6172416), Serial0/1/1
<output omitted>
P 10.10.14.128/25, 1 successors, FD is 6026496
via 172.16.1.38 (6026496/2172416), Serial0/1/0 via 172.16.1.42 (7181056/28160), Serial0/1/1
<output omitted>
Figure 3(b)
Analyze the output shown in the above Figure 3(b).
i. Explain how DUAL algorithm chooses the best path to the networks 10.10.12.0/24 and 10.10.14.128/25.
ii. If the chosen path is suddenly down, explain what will happen.
(c) By default, Routing Information Protocol (RIP) updates are forwarded out of all RIP enabled interfaces. However, RIP updates really only need to be sent out to interfaces connecting to other RIP enabled routers. Explain what happens when RIP updates and sent out of Local Area Network (LAN) interfaces.
Question 4
(a) With the aid of a block diagram, explain how a router would choose the most appropriate route from its "ip routing table", while performing a routing lookup process to forward packets.
(b)
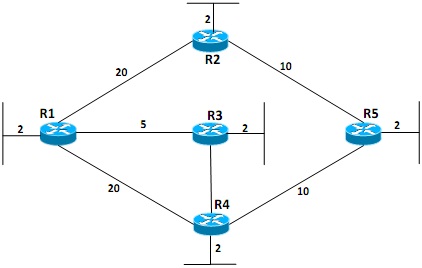
Figure 4(b)
Figure 4(b) shows the topology with each link cost. Construct the shortest Path First (SPF) tree for the router R1 using the Edsger Dijkstra's algorithm.
(c) Justify why most of the network designers and administrators prefer to use Link-State Routing protocols over Distance Vector protocol. (Provide any THREE (3) reasons).
Question 5
(a)
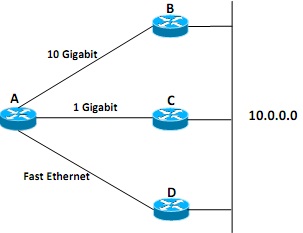
Figure 5(a)
All routers shown in Figure 5(a) are enabled with Open Shortest Path First (OSPF) with default setting. Router-A learns of the network 10.0.0.0 via routers B, C and D.
i. Analyze and explain the problems involved in building a routing table to route packets from router-A to the network 10.0.0.0.
ii. Propose your solution to solve the problems and explain the results of your proposed solution.
(b)
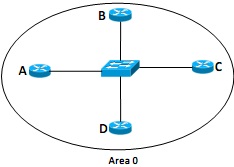
Figure - 5(b)
By default, OSPF routers exchange Link State Advertisements (LSAs) by flooding them to all OSPF neighbours and this action affects the performance of the Broadcast and Non- Broadcast Multiple Access topology shown in Figure 5(b). Explain how OSPF addresses this LSA flooding problem to enhance network performance.
(c)
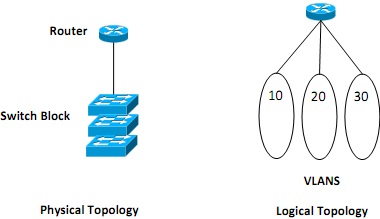
Figure 5(c)
You are assigned to implement and configure the above shown network segment in your organization. Discuss how would you configure and implement the routing between the users on VLAN 10, 20 and 30.
Question 6
(a) Discuss the first FIVE (5) steps of the complex algorithm of Border Gateway Protocol (BGP) to determine the best path while at the same time updating both the BGP Routing Information Base and routing table.
(b) With the aid of a diagram, explain how the Internet Assigned Numbers Authority (IANA) allocates an IPv6 Global Unicast Address to an organization.
(c) A Teredo client has the address 2001::62C3:1B8D:346B:EBC9:7C94:EA26. With reference to this IPv6 address, answer the following questions.
i. Is this client behind a cone NAT or a restricted NAT?
ii. What is the public IPv4 address of its Teredo server?
iii. What is the external IPv4 address?
iv. What is the UDP port number for this Teredo client's Teredo traffic?