Reference no: EM131059434 , Length: 1
Question 1
Given the following network in Figure 1, construct the routing table of router R1:
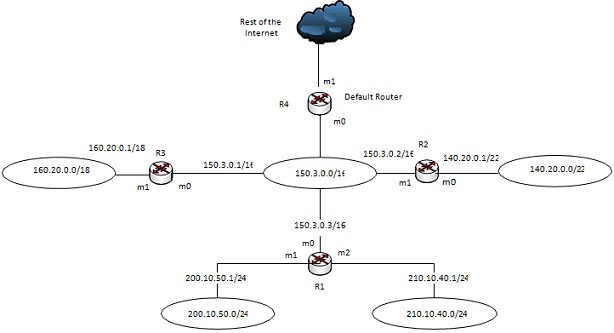
Question 2:
Consider the following UDP header dump:
BB400015003AFF10
a) Identify the source port number.
b) Identify the destination port number.
c) What is the length of the data?
d) Is it a packet from the client to the server or vice versa?
e) What is the client process?
Question 3
Given the following IPv6 addresses in hexadecimal colon notation, answer the following questions. Where applicable provide your answers in fully expanded hexadecimal colon notation.
a) What is the full (expanded) address of the abbreviated IPv6 address FDEC::CF:0:FFFF?
b) What is the type of block of the abbreviated IPv6 address 2001:A100:FC1::A4B8:AE12:3217:FCBA?
c) What is the type of address of the abbreviated IPv6 address 0::FFFF:194.42.12.7?
Question 4:
With reference to Domain Name System,
a) What is partially qualified domain name (PDQN), and what assumption is made by a DNS resolver when processing it?
b) Explain the difference between a DNS resolver and a DNS root server.
|
Products of inertia for rotation about the z axis
: Find its moment of inertia for rotation about the z axis. Without doing any integrals write down and explain its two products of inertia for rotation about the z axis.
|
|
Risk of excess components due to unmet forecasts
: Inventory management is a critical but yet sometimes the overlooked part of the purchasing and supply chain management. The fear is running out of materials that would shut down production, but there is a risk of excess components due to unmet for..
|
|
Turn circular loop of radius
: A 200 turn circular loop of radius 35 cm is lying flat on the ground with a current of 125 A circulating counterclockwise (when viewed from above) in a location where the Earth's field is pointed north, but at an angle 45.0° below the horizontal a..
|
|
How does your interview line up with the research
: Division of Labor in your Household: Write an essay in which you describe what the division of household labor was like in your own house growing up. Who did what, and how did everyone seem to feel about it? Were there tensions over who did wha..
|
|
Difference between a dns resolver and a dns root server
: COIT12206 TCP/IP Principles and Protocols - What is partially qualified domain name (PDQN), and what assumption is made by a DNS resolver when processing it and explain the difference between a DNS resolver and a DNS root server.
|
|
Hand on a clock that measures the seconds
: What is the rotational speed of the hand on a clock that measures the seconds?
|
|
How to practice native american spirituality
: The term ______________ refers to those New Age authors who claim the ability to teach their consumers how to practice Native American Spirituality.
|
|
Present in chlorine gas
: Chlorine gas (Cl2) forms when two chlorine atoms share an electron. What type of bonding is present in chlorine gas?
|
|
Eqq-economic order quantity
: Economic order quantity is commonly used in ordering parts for production.What is ECO? Include an example.What are the four assumptions on which economic-order quantities are based?
|