Reference no: EM131092284
Submit your assignment on-line using the course web page. No other form of submission will be accepted.
You are required to submit:
- PAP.pkt
- CHAP_no_good.pkt
- CHAP.pkt
- IPv6_route.pkt
- Task4.pkt
- IPv4_ACL.pkt
- IPv6_ACL.pkt
- Answer.txt
We will
- test run the Packet Tracer files;
- check configurations of the network devices;
You must
- use Packet Tracer 6.0.1 posted on the course web site. If you use other versions of Packet Tracer and we cannot run your file, you will get zero mark for the file. No resubmission is allowed.
- save and submit Packet Tracer files using .pkt format. Other formats including .pkz format will be ignored and you will get zero mark for the file. No re-submission is allowed.
- Do not set passwords to any file. Password protected files will be ignored and you will get zero mark for the file. No re-submission is allowed.
- put all your answers other than the Packet tracer files in answer.txt.
- use spaces for formatting. Do not use tabs. Do not attach images.
- save and store answer.txt in pure text format. No PDF, HTML, Word files, Open Office files, RTF etc. and no compression or archiving such as zip, rar or tar.
- submit 8 files. Do not compress or archive the 8 files using zip, tar or other utilities. Compressed or archived submission will be ignored and you will get zero mark for the assignment. No re-submission is allowed.
There are five tasks in this assignment.
Task 1
Question 1
If you cannot remember the enable password of a Cisco Router or a Cisco Switch created by the command “enable password USQ”, and there is no written record of it anywhere, is it possible for you to find out what the forgotten password is? If possible, outline the way to do so. You do not have to provide the Cisco router commands.
Question 2
Explain the use of the following three commands:
1. R(config)# enable password CSC3427
2. R(config)# enable secrete CSC3427
3. R(config)# enable service password-encryption
Question 3
USQCargo is an air cargo company based in Wonderland. It has scheduled delivery to 23 destinations worldwide. USQCargo has to monitor
- The where-about of all cargo in real time; the information will come from the delivery centres in each destination and in Wonderland.
- Local weather in each destination; the information will come from the local weather bureaus every hour.
- Local traffic conditions in each destination; the information will come from the local city traffic control centres every 15 minutes.
Select and justify in less than 100 words, your choice of WAN connection - leased line or Frame Relay, between The USQCargo headquarter in Wonderland and
a) the delivery centres in each destination;
b) the weather bureaus in each destination;
c) the city traffic control centres
Question 4
In less than 100 words, explain the major differences between
a) Circuit switching
b) Packet switching with switched virtual circuit
c) Packet switching with permanent virtual circuit
Question 5
Your company is using Cisco routers and switches.
If you are asked to use WAN link to link your company’s network to the network of another company with limited information available to you, which type of WAN encapsulation, HDLC or PPP would you use? Justify your answer in less than 50 words.
Question 6
When setting up ACL
a) What is the three Ps rule?
b) Where an extended ACL should be placed for best result?
Task 2
Both question 1 and question 2 refer to the topology show below:
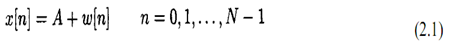
Question 1
Implement the given topology using Packet Tracer. Make sure that PC 192.168.1.1 can ping PC 192.168.2.1. Then implement PAP authentication for the serial PPP link between router Peter and router Paul. Name the file PAP.pkt.

Question 2 (10 marks)
a) Implement the given topology using Packet Tracer. Make sure that PC 192.168.1.1 can ping PC 192.168.2.1. Then implement CHAP authentication for the serial PPP link between router Peter and router Paul. Name the file CHAP_no_good.pkt.
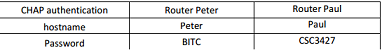
In less than 50 words, explain why PC 192.168.1.1 cannot ping 192.168.2.1 after implementing CHAP authentication for the serial link.
b) Make changes in CHAP_no_good.pkt so that the PCs can now ping each other and the routers are using CHAP authentication. You may need to turn off and on the serial link before the configuration changes are effective. Save the file as CHAP.pkt.
Task 3
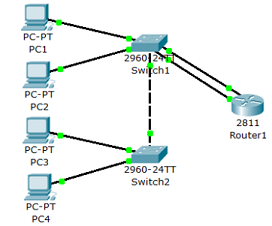
- Implement the topology using Packet Tracer:
- Assign VLAN and IPv6 global address to all PCs.
- Routing prefix for all PCs is 2400:DB00:2200::/64.
- Configure the router f0/0 as the interface for subnet 1 and f0/1 as interface for subnet
- Enable RIPng in Router1.
- Make sure that when the router fast ethernet interfaces are turned off, PC1 and PC3 cannot ping PC2 and PC4; and when the interface are turn on, all PCs can ping each other.
You may need to use the command line help facility (?) in Packet Tracer. Name the Packet Tracer file as IPv6_route.pkt.
Task 4
Task 4 refers to the following topology:
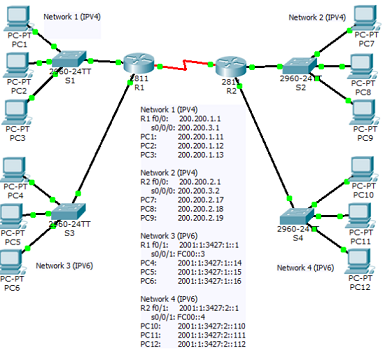
In the topology:
- All IPV4 networks used in the topology are class C networks.
- All IPV6 networks are using /64.
- PC1, PC2, PC3, PC7, PC8, PC9 can ping each other.
- PC4, PC5, PC6, PC10, PC11, PC12 can ping each other.
- R1 and R2 have IPV4 and IPV6 dual stack enabled.
Question 1
Implement the topology using Packet Tracer. Name the file Task4.pkt.
Question 2
Can PC1 ping PC4? Explain why.
Question3
Explain why NAT is not necessary in IPV6.
Task 5
Question 1(5marks)
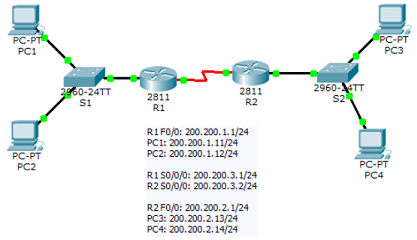
Implement the topology using Packet Tracer. Add extended, named, ACL such that:
- PC1 can ping PC2, PC3 but not PC4
- PC2 can ping PC1, PC4 but not PC3
- PC3 can ping PC4, PC1 but not PC2
- PC4 can ping PC3, PC2 but not PC1
Name the file IPv4_ACL.pkt.
Question2
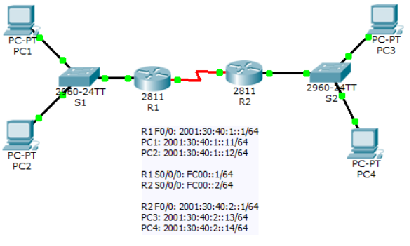
Implement the topology using Packet Tracer. Add ACL such that:
- PC1 can ping PC2, PC3 but not PC4
- PC2 can ping PC1, PC4 but not PC3
- PC3 can ping PC4, PC1 but not PC2
- PC4 can ping PC3, PC2 but not PC1
You have to find the commands and syntax for applying ACL in IPV6. Name the file IPv6_ACL.pkt.