Consider the following case study:
In order to avoid criticisms of their existing manned road-toll payment system on its private road, WS-Pass has decided to adopt an automated toll paying system. The new system uses RFID technologies where each subscriber is given an RFID tag designed to be carried on the windshield of their vehicle. The reader antennas are mounted on a gantry approximately 20 feet above the roadway and all the transactions are sent to a database server, as shown in the following diagram.
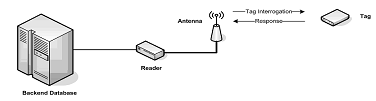
Answer the following questions based on the above scenario.
(a) What type of RFID tag is more appropriate for WS-Pass? Justify your answer.
(b) Discuss on how complacency can cause serious security problems to WS-Pass in the future.
(c) Give one typical use of RFID technology, other than road toll payment.
(d) On a rainy night, an attacker decides to temporarily disable his tag before driving through the toll booth.
i. Elaborate on two techniques which the attacker can adopt to physically disable the RFID tag for a temporarily basis.
ii. Discuss on one technique that WS-Pass can adopt in order to prevent such incidences from occurring whereby ensuring that every car is charged the toll fee.
(e) Unauthorized tag reading has often been a security challenge for RFID systems.
i. By making reference to the diagram, explain how an attacker can secretly read particular tags.
ii. Describe two mechanisms that can be adopted to enforce confidentiality during transmission by RFID components.
(f) Briefly discuss on the following types of attacks possible on WS-Pass system.
i. Crypto attacks
ii. Covert channels