Reference no: EM131370260
Problem 1: Let k ≥ 32 be a positive integer, and let n =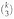 . Consider the k x n binary matrix G whose columns are all the
. Consider the k x n binary matrix G whose columns are all the 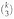 binary vectors of length k and hamming weight 3. Let C be the (n, k, d) binary linear code generated by G. What is the minimum distance d of C? Prove your answer.
binary vectors of length k and hamming weight 3. Let C be the (n, k, d) binary linear code generated by G. What is the minimum distance d of C? Prove your answer.
Hint: Let x ∈ C be the sum of some s rows of G. Consider the weight of x as a function of s.
Problem 2: In this problem, we use the term perfect code to refer specifically to an (n, M, d) binary code (either linear or nonlinear) with u = 2m - 1, M = 2n-m and d = 3, for an integer m ≥ 3. An extended perfect code C* is a code of length n + 1= 2m obtained from a perfect code C of length n by appending an extra coordinate, so that the weight of all the code words in C* is even.
a. Let C ⊂ F2n be a perfect code. Prove that there exists a partition C0, C1, . . . , Cn of F2n into perfect codes, where C0 = C and Ci = ai + C is a translate of C for i = 1, 2, . . . , n.
b. Let E2n+1 be the set of all even weight vectors in F2n+1. Show that, given an extended perfect code C* ⊂ E2n+1, there exists a partition C*0, C*1, . . . , C*n, of E2n+1 into translates of C*, with C*0 = C*.
c. Let C0, C1, . . . , Cn and C*0, C*1, . . . , C*n be partitions of F2n and F2n+1 as in parts (a) and (b) above. Let π be an arbitrary permutation on the set {0, 1, . . . , n}, and let (a|b) ∈ F22n+1 denote the concatenation of a ∈ F2n+1 and b ∈ F2n. Prove that the code ϑ defined below is perfect:
ϑ =def {(c*|c) : c*∈ C*i, c ∈ Cj, π(i) = j}
d. Use the construction in part (c) to show that, for all m ≥ 4, there exist nonlinear perfect codes of length n = 2m - 1.
e. Prove that there are at most 2m2^n-m distinct perfect codes of length n = 2m - 1. Here, codes C and C' are considered distinct if the set of codewords of C differs from the set of codewords of C'.
Problem 3: The decay function D from Fqn to Fqn-1 is defined as follows. Each vector x = (x1, x2, . . . , xn) in Fqn is mapped by D into the vector:
D(x) = (x2 - x1, x3 - x2, . . . , xn - xn-1)
The lifespan of a vector x ∈ Fqn is defined as the smallest integer i such that Di(x) = 0; that is, applying the decay function D to x successively i times results in the all-zero vector of length n - i. If no such i exists, then the lifespan of x is defined to be n. The lifespan of the vector 0 is zero, by convention.
a. Prove that if x1 is a vector of length n and lifespan i, and x2 is vector of length n and lifespan j, with j < i, then x1 + x2 is a vector with lifespan i. That is
lifespan (x1 + x2) = max {lifespan (x1), lifespan (x2)}
b. Suppose it is known that the lifespans of the k vectors x1, x2, . . . , xk ∈ Fqn are are all distinct. Prove that these k vectors are linearly independent over Fq.
c. Let ∝ be a primitive element of Fq, and let x1 and x2 be two vectors of lifespan i in Fqn. Prove that there exists an integer j ∈ {0, 1, . . . , q-2} such that lifespan (xi + ∝jx2) < i.
d. Given a linear code C of length n and dimension k over Fq, let Li denote the number of codewords of lifespan i in C. The integers L1, L2, . . . , Ln are called the lifespan distribution of C. Prove that the lifespan distribution of any such code C contains exactly k nonzero values.
e. Define the cyclic decay function D' from Fqn to Fqn as follows. Each vector x = (x1, x2, . . . , xn) in Fqn is mapped by D' into the vector:
D'(x) = (x2 - xi, x3 - x2, . . ., xn - Xn-1, x1 - xn)
The lifespan with respect to this function is defined as before. Namely, cyclic-lifespan (x) is the smallest integer i such that applying the cyclic decay function D' to x successively i times results in the all-zero vector of length n. In this part, assume that n is a power of 2 and q = 2. How many binary vectors of length n and cyclic lifespan i are there, for each i = 0, 1, . . . , n?
Problem 4: In this problem, we deal with three different finite fields: the ground field GF(q), its extension GF(qm) of degree m, and the extension of GF(qm) of degree n, namely the finite field GF(qmn). Throughout this problem, assume that n divides q - 1.
a. Prove that the polynomial xn - 1 has n distinct roots in GF(q).
b. Prove that for any finite extension GF(qm) of GF(q), there exists a primitive element β ∈ GF(qm) such that {β, βq, βq^2, . . . , βq^m-1} is a basis for GF(qm) over GF(q).
c. Now let y be a primitive element of GF(qmn) such that {γ, γq, γq^2, . . . , γq^nm-1} is a basis for GF(qmn) over GF(q). You have proved in part (b) that such an element exists. You have also proved in part (a) that all the n distinct roots of the polynomial xn - 1 lie in in GF(q). Let us denote these roots by e1, e2, e3, . . . , en. Define n elements ∝1, ∝2, . . . , ∝n ∈ GF(qmn) as follows:
∝i =def γ + (γq^m/ei) + (γq^2m/ei2) + . . . + (γq^(n-1)m/ein-1) for i = 1, 2, . . . , n
Prove that the elements (∝1)n, (∝2)n, . . . , (∝n)n lie in the subfield GF(qm). That is, show that (∝i)nq^m = (∝i)n for all i = 1, 2, . . . , n.
Hint: First show that this holds for n = 2, with q odd and e1 = 1, e2 = -1.
d. Prove that the elements in the set
B =def {(∝i)q^i ∈ GF(qmn) : for i = 1, 2, . . . , n and j = 0, 1, . . . , m - 1}
are linearly independent over GF(q). Therefore, conclude that the set B is a basis for GF(qmn) as an mn-dimensional vector space over GF(q).
Problem 5: Let C be a binary linear cyclic code of length n with zeros at {∝Z1, ∝Z2, . . . , ∝zr}, where ∝ ∈ GF(2m) is a primitive n-th root of unity. That is C = (g(x)), where deg g(x) = r and the r roots of g(x) are precisely ∝Z1, ∝Z2, . . . , ∝zr. For any subset I = {i1, i2, . . . , iμ} of {0, 1, . . . , n-1} define the code
C(I) = { (ci1, ci2, . . . , ciμ) : (c0, c1, . . . , cn-1) with ci = 0 for all i ∉ I is in C }
In other words, C(I) is the code obtained from C by shortening Cat all the positions that are not in I. Throughout this problem, assume that n = n1n2 is an odd composite integer.
a. Write down a parity-check matrix for C(I).
b. Let β ∈ GF(2m_1) be a primitive n1-th root of unity, where m1 is the least integer such that n1 divides 2m_1 - 1. Prove that β ∈ GF(2m), where m is the least integer such that n divides 2m - 1.
c. For I = {0, n2, 2n2, . . . , (n1 - 1 )n2}, show that C(I) is a cyclic code and find the set of zeros of C(I) in terms of {z1, z2, . . . ,zr} and β. In particular, if C is a narrow-sense BCH code of length n1n2 = 31·3 = 93 with designed distance 11, express the zeros of C and C(I) as unions of cyclotomic cosets modulo 93 and 31, respectively. What is the dimension of C(I)?
d. Now let C be a BCH code with zeros at ∝0, ∝1, . . . , ∝δ-1 and their conjugates. Let I1, I2 be such that {∝i : i ∈ I2} = {∝a + ∝i : i ∈ I1} for some fixed a. Show that C(I2) = C(I1).
Problem 6: Throughout this problem, let BCH(n, q; δ) denote a narrow-sense BCH code of length n with designed distance δ over the finite field GF(q). Further, assume throughout that n and q are relatively prime, and let m denote the least integer such that n divides qm - 1.
a. Let C be a linear cyclic code of length n over GF(q), and let Z denote the set of zeros of C. That is C = (g(x)), and Z is the set of exponents of all the zeros of g(x). Prove that C contains its dual code C⊥ if and only if Z ∩ Z-1 = ∅, where Z-1 =def {-z mod n : z ∈ Z}.
b. In this part, assume that n = q - 1. Show that BCH(n, q; δ)⊥ ⊆ BCH(n, q; δ) if and only if δ ≤ (n+1)/2, where BCH(n, q; δ)⊥ denotes the dual code of BCH(n, q; δ).
c. Prove that if δ ≥ q√n, then BCH(n, q; δ)⊥ ? BCH(n, q; δ)
Hint: Express the length n in base q, namely write n = n0 + n1q + · · · + nsqs for some s.
d. Now let us consider binary BCH codes only. Suppose that n > 2⌊m/2⌋ and δ ≤ n2⌊m/2⌋/(2m - 1). Show that under these conditions, we have
dimBCH(n,2; δ) = n - m ⌈δ-1/2⌉.