Reference no: EM131099689
Network Proposal
Overview
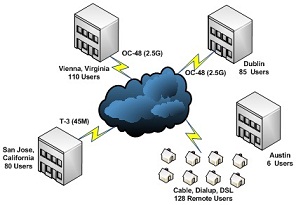
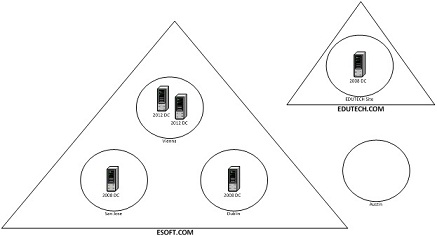
EchoSoft is an educational software developer that provides software and cloud computing solutions to private and public educational institutions throughout North America and Europe. The organization currently has four major offices located in Vienna, Virginia, San Jose, California and Dublin, Ireland. A sales team of more than a hundred work across the United States and Europe, primarily from their own homes. EchoSofthas experienced a combination of growth and disaster in the last 3 years and plans to add an additional 130+ employees, including opening a new office in Austin Texas in the next 6 months. To meet these growth challenges,EchoSoftis in the process of upgrading the network environment from the current adhoc design,comprised of Windows 2003, 2008 and *NIX systems, to Windows 2012R2 Active Directory. Steps have already been taken to improve the network infrastructure. The Vienna Virginia location has replaced all 2008 Domain Controllers with Windows 2012 Servers. However, the San Joseand Dublinlocationsare still running a single Windows 2008 Domain Controller at each site. Currently all server and workstation IP addresses are statically assigned. DNS is hosted on an older generation UNIX server that has been hacked several times due to faulty security. Remote users currently connect via VPN, which has caused numerous security incidents due to missing antivirus software, outdated AV signatures and missing OS patches on workstations and laptops.
Although the Austin location has not officially opened there are six users currently deployed to that location. There are currently no domain controllers or qualified personal to support them at this location. This site needs to be incorporated into the EchoSoftActive Directory ASAP. Austin users must be able to authenticate and access EchoSoftActive Directory services. EchoSofthas recently acquired another company EduTech Inc. The existing EduTechActive Directory Domain needs to be integrated into the existing EchoSoftActive Directory forest. The EchoSoftdata center is located at the Vienna and Dublin locations. This is where EchoSofthosts and maintains its cloud computing services. Due to increased demand for its cloud services EchoSofthas experienced difficulty getting servers and services deployed in time due to the lack of an efficient and cost-effective deployment process. The current Active Directory is a single domain. It is up to you finish the network design and improve the server infrastructure.
Current Physical Locations
Current Logical Design
Required Proposal Responses
Executive Overview - Provide an executive overview for Infrastructure proposal. How will your proposal help EchoSoft? What are the key aspects of your design? Why should EchoSoftselect your proposal over your competitors' proposals?
Develop a Windows Deployment Design and plan an automated client workstation and server installation strategy. This objective can include but is not limited to: images and bare metal/virtual deployment; plan for multicast deployment and plan for Windows Deployment Services (WDS).This solution should enable EchoSoftto deploy client and server operating systems in a timely and cost-effective manner.
Plan and deploy Virtual Machine Manager Services. This objective may include but is not limited to: Design Virtual Machine Manager service templates; plan and deploy profiles including operating system profiles, hardware and capability profiles, application profiles, plan and manage services including scaling out, updating, and servicing services; configure Virtual Machine Manager libraries. This solution should enable EchoSoftto deploy servers in a timely and cost-effective manner.
Windows Server Design - Vienna has two Domain Controllers. All other locations have single Domain Controllers. Vienna's domain controllers are running Windows Server 2012, but the other sites are running Windows Server 2008 Domain Controllers. All other services on the network are running on either older UNIX or Windows Server 2008 and 2003 servers. These legacy servers should be replaced as part of this project. Describe your recommendations for the server environment, focusing on any needed upgrades and the number of servers needed at each location to handle key network infrastructure services and roles (DNS, DHCP, File, Print, RRAS, etc.) You can make any recommendation for the server environment but explain how it will benefit your design.
Design and maintain a Dynamic Host Configuration Protocol (DHCP) solution. This objective may include but is not limited to the following: Design considerations including a highly available DHCP solution including split scope, DHCP failover, and DHCP failover clustering, DHCP interoperability, and DHCP filtering. Describe how you will provide fault tolerance in the event that a primary DHCP server should fail. How will you handle remote users, network devices and printers?
DNS - Design a name resolution strategy. This objective may include but is not limited to: Design considerations, including Active Directory-integrated zones, DNSSEC, DNS Socket Pool, cache locking, disjoint namespaces, DNS interoperability, Single-Label DNS Name Resolution, zone hierarchy, and zone delegation.
Implement a scalable Remote Access solution. This objective may include but is not limited to: Configure site-to-site VPN; configure packet filters; implement packet tracing; implement multisite Remote Access and a DirectAccess solution.
Design an Active Directory topology. This objective may include but is not limited to: Design considerations including read-only domain controllers (RODCs), proximity of domain controllers, replication optimization, and site link; Group Policy, monitor and resolve Active Directory replication conflicts.
Your proposal must incorporate the following items
1. All Domain Controllers must be Windows 2012 2R2 Active Directory.
2. All sites must have Active Directory services available even if a single Domain Controller fails.
3. Client IP address assignment must be automated and manageable for all sites and locations.
4. DNS must be manageable and secure. Clients must be able to resolve DNS even if a single DNS server fails or during aninternet connection outage.
5. DHCP should be designed with fault tolerance in mind.
6. Provide secure remote access solution that utilizes Network Access Policy controls.
7. Provide easy and manageable workstation image and software deployments. All workstations should be Window 8.
8. Provide easy and manageable server image and software deployments. All servers should be Windows Server 2012 R2.
9. EduTech and EchoSoftActive Directory forests must be able to trust each other.
10. The Austin location needs be integrated into the EchoSoftActive Directory. This solution must cost-effective, manageable and secure.
Assignment Requirements
There are specific requirements for the assignment: The final submission should contain at least 7 pages' worth of text written by the student (not counting title page, images, diagrams, tables, or quotations), but may be longer, not to exceed approximately 10 pages' worth of student-supplied text. (With the required diagram, and other images, title page, etc., the final submission may end up being more than 10 pages in length.) It must be double-spaced, have 1-inch margins, and use 12-point Times New Roman or 10-point Arial/Helvetica font. A title page is required; APA format for the title page is optional.
• At least one diagram must be included (not counted towards the minimum length described above); this could be a diagram describing Active Directory components, DHCP/DNS design, or anything else that is worth displaying graphically to enhance the reader's understanding of the proposal. Additional diagrams, images, or tables are welcome.
• The submission must cover all of the major topics outlined above. Each choice should be explained with technical and business reasoning. The solution should be reasonably detailed. Additional topics may be covered as desired.
• The structure of the final submission is flexible. There is no specific format required, although it should be organized logically and represent a single, unified solution. It is likely that the format will include separate sections for each of the topics required, as well as a summary.
• At least two non-Lab, non-Wikipedia reference is required; preferably, this would be a "best practice" guide or similar content from Microsoft or an experienced provider of Microsoft solutions.
• Be sure to properly quote or cite any sources used. APA format is required for in-text citations and the list of works cited at the end. It is expected that you are already familiar with"Policy on Academic Dishonesty and Plagiarism." It is available in the Academic Policies section of the Syllabus; there are also links in the Webliography. In its simplest form, if you are using text from a source, you must cite and/or quote it.