Reference no: EM13971153
Project: Prepare a Policy to Combat Advanced Persistent Threats
Introduction
Advanced Persistent Threats (APT) have become an area of great concern for businesses and government organizations. APTs are used by attackers to gain entry into an organization's networks and then remain inside by avoiding detection for extended periods of time during which information is harvested and exfiltrated. (See the infographic at https://www.symantec.com/theme.jsp?themeid=apt-infographic-1 )The threat agents for APTs are frequently software-based (malware) agents which can hide on servers and workstations for years before being activated. Since these agents are inside the defensive perimeter for the enterprise, they can be categorized as a type of insider threat. Many of the strategies to combat insider threats can also be used to detect and respond to APTs (see Nigel Wilson's blog at https://nigesecurityguy.wordpress.com/2014/03/17/apt-strategy-guide/)
Table 5-1. Best Practices for Combating Advanced Persistent Threats (adapted from https://nigesecurityguy.wordpress.com/2013/11/08/apt-strategy-series/)
• Maintain a list of application systems at risk
• Create an APT checklist for assets at risk
• Focus on APT detection techniques and analysis tools
• Focus on incident response for APTs
• Create ready to use APT rapid response tactics
• Prepare an APT forensic response plan
• Increase use of external threat intelligence
• Focus on APTs in security awareness training
In earlier projects for this course, you developed IT security policies for a specific organization. You may use applicable information from those projects when preparing the deliverable (APT policy) for this assignment.
If you wish to change to a different organization for project #5, you must first obtain your instructor's permission.
YourAPT security policy will be used to implement best practicesfor combating APT threats against the information, information systems, and information infrastructure (e.g. networks, communications technologies, etc.) which are housed within the data center. These best practices should include both administrative actions and implementation of technology-based defensive measures (e.g. real-time monitoring, host-based intrusion detection / prevention, etc.).
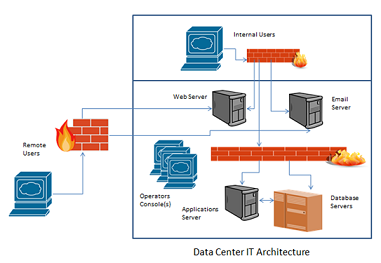
Your policy is being written by you as the facility manager. In this role, you are also the information system owner (ISO) for all IT systems and networks within the data center. The information systems hosted in the data center are shown in Figure 5-1.
The primary audience for your policy is the Tier 1 staff responsible for day-to-day operations and maintenance in the data center. Your policy will be communicated to other personnel and to the senior managers who are ultimately responsible for the security of the organization and its IT assets. These managers include: CEO, CIO/CISO, and CSO.
Research:
1. Research the subject of APTs as threats to the security of the information, information systems, and information infrastructure within the data center.Here are three URLs to start with:
a. https://nigesecurityguy.wordpress.com/2013/11/08/apt-strategy-series/
b. https://nigesecurityguy.wordpress.com/2014/03/17/apt-strategy-guide/
c. https://nigesecurityguy.wordpress.com/category/governance/
Note: some APT reports can only be accessed after registration (provide contact information). You are not required to use these reports but, some of the better examples are:
a. https://www.secureworks.com/resources/articles/featured_articles/20120719-hcr/
b. https://www.isaca.org/Knowledge-Center/Research/ResearchDeliverables/Pages/Advanced-Persistent-Threats-Awareness-Study-Results.aspx
c. https://securityintelligence.com/media/2014-ponemon-study-economic-impact-advanced-persistent-threats-apts/
2. Use the list presented in Table 5-1 and the IT architecture shown in Figure 5-2 to identify the types of information, information systems and information infrastructures (networks) which may be targeted byAPTs. Create a list of ten to fifteen specific areas of weakness or vulnerability ("risks") which could be exploited by an APT to gain access to or harvest information from the IT resources shown in this diagram. Include software applications in your informationsystems category.
3. Assess / evaluate the potential harm that could occur if the identified weaknesses or vulnerabilities are exploited by an APT. Use this information to prioritize your list of risks. Document the risks, potential impacts, and response priorities in a risk register(See Table 5-2). You will include this risk register in your policy deliverable for this assignment.
4. Identify at least 10 control measures or mitigations which could be used to address the identified risks. Use Table 5-1 and NIST 800-53 as your starting points.
5. Identify 5 or more technologies which can be deployed to implement detection, prevention, and eradication of APTs.
Table 5-2. Risk Register
|
Risk Identifier
|
Description of the Risk
(identify affected assets)
|
Response Priority
(Most important = 1)
|
|
Sequence # or Brief title (<50 characters)
|
Split complex risk statements into multiple individual risks.
|
|
|
|
|
|
|
|
|
|
Figure 5-3. Data Center IT Architecture Diagram
Write:
1. Use the outline below to prepare your APT security policy for the data center.You must include 10 to 15 specific policy statements which address the prevention, detection, and eradication of Advanced Persistent Threats. You must also include your risk assessment and risk register (prepared earlier) containing 10 to 15 specific risks. Your mitigation strategies must include at least 5 technology-based countermeasures (technical controls) (including identification of 5 or more specific technologies).
I. Identification
a. Organization: [name]
b. Title of Policy:
c. Author: [your name]
d. Owner: [role, e.g. Data Center Manager]
e. Subject:
f. Review Date: [date submitted for grading]
g. Signatures Page: [authorized signers for the policy: CEO, CISO, Data Center Manager]
h. Distribution List
i. Revision History
II. Purpose
a. Provide a high level summary statement as to the policy requirements which are set forth in this document.
III. Scope
a. Summarize the information, information systems, and networks to be protected.
b. Identify who is required to comply with this policy. See the project description for categories of personnel and other individuals.
IV. Compliance
a. Identify the measures which will be taken to ensure compliance with this policy (e.g. audits, compliance reporting, exception reporting, etc.)
b. Identify the sanctions which will be implemented for compliance failures or other violations of this policy.
c. Include information about how to obtain guidance in understanding or interpreting this policy (e.g. HR, corporate legal counsel, etc.)
V. Terms and Definitions
VI. Risk Identification and Assessment
a. Using your risk register, present the findings of your risk assessment.
b. Using Table 5-1 and NIST 800-53 as starting points, identify control measures and protective solutions (technologies) which will be implemented to mitigate or otherwise address each risk or risk area (you may add a column to your risk register table or present in paragraph format).
VII. Policy
a. For each control measure, write a policy statement ("Shall" wording) which addresses the implementation of that control.
b. Include an explanatory paragraph for each policy statement.
2. Prepare a Table of Contents and Cover Page for your policy. Your cover page should include your name, the name of the assignment, and the date. Your Table of Contents must include at least the first level headings from the outline (I, II, III, etc.).
3. Prepare a Reference list (if you are using APA format citations & references) or a Bibliography and place that at the end of your file. (See Item #3 under Formatting.) Double check your document to make sure that you have cited sources appropriately.