Reference no: EM133347
QUESTION 1
Examine the concept of Data, information and knowledge in information warfare.
QUESTION 2
The progression of writing of documents including corporate safekeeping policies, standards & procedures can be quite lengthy and necessitates course and surely THREE questions comes back on the plate. Confer those three questions?
QUESTION 3
Distinctiveness theft rates one of the fastest growing crimes today and the Internet can make it even easier for some law breakers to take your good name and drag it through the mud. What would be some practical tips on how to avoid having ID stolen?
QUESTION 4
As of the myriad motives behind politically motivated computer misdeeds and the level of media hype, it is often not easy for executives and safekeeping professionals to appreciate and manage the threat. This puzzlement makes it easy to either over or under react. Several trends are clear and should be considered when assessing the risk from politically stimulated computer crime. What are they?
PART II
CASE STUDY: McClintock Manufacturing
Prologue (Introduction) of the Decision Maker and Problem
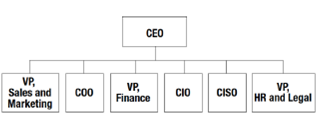
You are the chief information safekeeping officer (CISO) of McClintock Manufacturing, one of the largest manufacturing corporations in the world. With its corporate headquarters in London, UK, McClintock has branch offices in Hanover, Germany; Barcelona, Spain; Singapore; Hong Kong; and St. Louis, Missouri, USA. You have nine full-time safekeeping staff members; all but two report in a straight line to you, with one staff member at each branch office and the remaining four in London. You report unswervingly to the chief executive officer (CEO) and are part of the managerial team. You have been with McClintock for three and a half years.
Background Information
Company
McClintock Manufacturing is a widely held company that traces its roots to the beginning of the 20th century. McClintock has been gainful for all but a few years of its existence, even though profits have been down during the wide-reaching recession over the last two years. This company has approximately 9,000 employees and a few hundred long-term contractors. McClintock makes a wide multiplicity of small, durable goods and is known worldwide not only for the goods that it makes, but also for the excellence of those goods. Additionally, several times in the past, this corporation has invented ways to create new and better versions of existing products. McClintock's executive administration and the board of directors have a philosophy that they will not rush any product to the market. Instead, they have established processes in which each new product is carefully and thoroughly tested before it is allowed to go on the marketplace and quality assurance and McClintock go hand-in-hand.
The Board
The CEO is also the chairman of the board of directors, who rules with an iron hand and take on people to the board on the basis of their ostensibly being keen to give approval for initiatives with little delay. Consequently, the board is not a very purposeful entity: It provides little oversight and supervision to the business.
Finances McClintock Manufacturing is a publicly owned company within 2009 revenue of £201 million and a profit of £15.1 million. This concern has no significant debt and is considered a ‘class A' investment in the London stock market.
Marketing McClintock Manufacturing has a modest advertising campaign; people in the UK (and to a lesser degree, Europe at large) have heard of this business, although the company is also not exactly a family circle name within the UK. McClintock is also not all that much of an internationally known entity. The CEO has been deliberating whether the marketing efforts should be made stronger.
Industry
The manufacturing arena has taken a downward turn over the last two years. One of the effects of the bad economy has been a sharp drop in sales of manufactured goods. The level of rivalry within the manufacturing industry is very high, and a number of manufacturing companies have been selling manufactured possessions at below their actual cost because their inventories of manufactured goods have been high and also as of the need for greater cash flow.
Business Unit and Its Position (place) within the Company
Business units are the backbone of this company. Except for the way they share machinery and equipment used in manufacturing, each is a fiercely independent silo with the mission of being as profitable as possible. Business unit managers are highly valued and are placed high in the organisational chart; all of them report to the chief operations officer (COO). Each business unit faces what often turn out to be strict time deadlines. Business unit administrators must carefully plan their use of machinery and equipment within each plant because several selling units may conceivably need machinery and equipment at the same time. In addition, the machinery and equipment need to be available on a 24/7 basis. All machinery and equipment are controlled by process automation software on computers that run in control rooms. This software is shared out to the point (face) that any kind of network disruption or outage is likely to adversely affect production of goods. Issues
That Cause the Current Tension
You are commencement to realise that the information safekeeping role at McClintock Manufacturing does not have much influence and leverage, despite great effort on your part to communicate with managers from other functions and despite a positively regarded safekeeping training and awareness Programme. For example, you recently found out that no one from information safekeeping was invited to a series of meetings concerning changes in company operations. The fact that trade units, for the most part, function as silos elucidates more than anything else why business unit managers seldom initiate communication with you, but during budget meetings, you heard quite a few executives (the CEO included) make statements to the effect that they were not sure of the value that information safekeeping contributes to the company.
Furthermore, you have not been invited to a board meeting to present updates concerning the information safekeeping Programme in more than one year. The CEO is Stephen Wingate, a highly skilled, knowledgeable and visionary person. A perfectionist for dashboards and numbers, he constantly seeks more information concerning how the company is functioning, including sales of products, profit/loss statistics from the business units, efficiency of operations, status of compliance initiatives and much more. In fact, he is the most situation ally aware CEO for whom you have ever worked. He also is a genius in separating the ‘wheat from the chaff', i.e., deciding whether information he obtains is valuable and germane. Naturally, this also applies to information related to information safekeeping and the information safekeeping practice itself. In addition to, although he is not the inventor type, he is unusually apt in finding such people, hiring them and rewarding them richly. Stephen's stubbornness is his Achilles heel; he thinks and acts as if he is always right. In addition, his ‘get what you must do tomorrow done today' attitude significantly augments the stress levels of those who interact with him (yourself included), and he is over and over again less than courteous and respectful to those around him. Still, he is in charge for the company's profitability and success more than anyone else, and if he were to go from the company, finding someone of his calibre to put back him would be extremely difficult.
There are 19 business unit managers, of which the one who is probably the most typical is Deborah Peterson. Commonly, she comes into work early every morning and leaves late every night. She is enormously knowledgeable not only about business, but also about manufacturing and what discriminate a good product from a bad one. She has brought in a number of exceptional project managers who ‘toe the line' as regards project milestones and deliverables. From her standpoint, her business unit is the only thing that exists within the corporation, and she spends as little time as possible communicating with others who are not part of this unit, you very much included. An ambitious person, she can be very rough and edgy at times, and she, like the CEO, can quickly determine what is real and what is not.
QUESTION 5
Surroundings of the Decision Maker You know what you are doing. You have a bachelor's degree in IT and achieved your MSc in Computer Safekeeping & Forensics 3 years back. You have also just recently accomplished your CISM.
The Problem
You are beginning to realise that the information safekeeping practice that you set up three years ago is starting to show its age. Although you have tried to adjust this programme according to changes that have occurred within McClintock Manufacturing, you now realise that some areas have not been sufficiently considered. One of these areas is information safekeeping metrics. At the moment, the following types of metrics are used to measure the success of your information safekeeping practice:
a. Percentage of Windows systems that run antivirus software that is updated each day
b. Percentage of incoming network traffic that is evaluated by a firewall on an exterior gateway
c. Percentage of network traffic that is monitored by an intrusion detection system (IDS)
d. Percentage of systems that are patched within the required time period
e. Percentage of systems that are in compliance with McClintock's baseline safekeeping standards
f. Percentage of spam that is deleted by McClintock's spam wall
You now know that metrics you thought were ‘bulletproof' three years ago are no longer servicing the purpose that you assumed they originally had. Although your current metrics framework is not bad, you comprehend that enhanced metrics would more suitably serve your information safekeeping governance framework?
a) What are the chief (key) questions that should be asked?
b) The development of additional and more business relevant metrics is bound to help your information safekeeping practice be better aligned with both McClintock Manufacturing's business goals and, in particular, the needs and wishes of this company's executive management team, some of whom are questioning the value of information safekeeping. You have much to gain and little to lose. If you successfully complete this new endeavor, you are likely to increase information safekeeping's perceived value to its previously more valued status within your company than if you do nothing. In contrast, if you do nothing, your situation as leader of the information safekeeping practice is likely to continue to deteriorate (worsen). Thus, you have everything to gain, and very little to lose. Using figure 3, you need to create additional metrics. You must augment your current set of information safekeeping metrics with others that more meaningfully reflect how and what information safekeeping contributes to McClintock Manufacturing's business and its business and working (operational) processes. (Hint: Consider which of the confidentiality, integrity and availability (CIA) triad is most important to your company's business interests and devote additional thinking to the kind of information safekeeping metrics that naturally flow from the business considerations involved.) You must also express the rationale for each new metric you choose.
Alternatives With Pros and Cons of Each The rationale for each additional metric (and possibly also the elimination of certain metrics) that you decide on must include a discussion of the pros and cons associated with the change. For instance, you may make a decision to include a new metric, ‘percentage of time plant process control systems are alive and well 24/7'. The pros are intuitive. The cons are that, although this metric reflects critical commerce processes, it does not take into account conditions in which no business unit needs these systems.
Exhibits With Background Information High-level Organisational Chart